Metallic Documentation
No matter where your data is or where you want to store it, Metallic has a solution.
Going to the Hub
Go to the Hub for an overall picture of the health of your Metallic environment. The Hub is also the place to configure new data sources to back up.
Procedure
- Go to https://login.metallic.io/ and log in. The Hub appears.
- To determine the health of the environment, select from the following tabs, and then review the information in the tiles:
- Metallic Core
- Office 365
- Endpoints
- To back up a new data source, in the upper-right corner of the page, from the New Configuration list, click the type of data that you want to back up, and then follow the instructions in the guided setup.
Use cases
| Data source | Data source location | Backup storage location |
|---|---|---|
| File servers SQL servers | Cloud | Cloud |
| File servers Endpoints SQL servers Virtual machines | On-premises | Cloud On-premises On-premises and cloud |
| Office 365: Exchange OneDrive SharePoint | Cloud | Cloud |
To learn more about choosing a storage option, see All about storage.
Creating an administrator
You can create additional administrators for Metallic. When you set up Metallic, one administrator account is automatically created. If you use the Endpoint application and need to authenticate laptop and desktop users, see Endpoint tasks.
Procedure
- From the navigation pane, go to Security > Users.The Users page appears.
- In the upper right corner of the page, click Add user. The Add user dialog box appears.
- Next to User type, click Local user, and then provide the user information.
- From the User group list, select Tenant Admin.
- Decide how to create the password for the user:
- To auto-generate a password for local users, select the Use system generated password check box.
- To manually set a password for the user, in the Password box and the Confirm password box, type a password.
- Click Save.
Editing User Details
You can edit a user to update details, such as the email address and the user group.
Procedure
- From the navigation pane, go to Manage > Security > Users.
The Users page appears. - In the User name column, click the user that you want to edit.
The user details page appears. - On the Overview tab, in the upper-right corner, click Edit.
The Edit user dialog box appears. - Update the user information.
- Click Save.
Configuring identity provider
To authenticate users with SAML, configure an identity provider. Common SAML identity providers include AD FS, Azure, and Okta.
Note: The direct access method for Active Directory is not supported.
Using Azure Active Directory as Your Identity Provider
Azure Active Directory (Azure AD) is a third-party identity provider (IdP) that can act as the IdP when your users log on to Metallic. Metallic is the service provider (SP).
To integrate with Azure AD, add a SAML application in your Azure AD account and in Command Center. Metadata from the Azure application (IdP) and the Command Center application (SP) are shared during this process.
Before You Begin
You must have the Azure Active Directory Premium P1 or Premium P2 edition. For information, go to the Microsoft Azure Active Directory documentation.
Step 1: Creating an Application in the Azure Portal
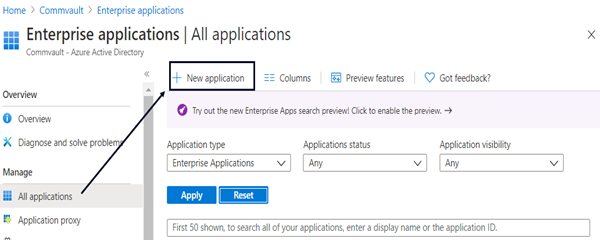
- Go to the Microsoft Azure portal.
- From the navigation pane, go to Azure Active Directory > Enterprise applications, and then click New application (
 ).
).
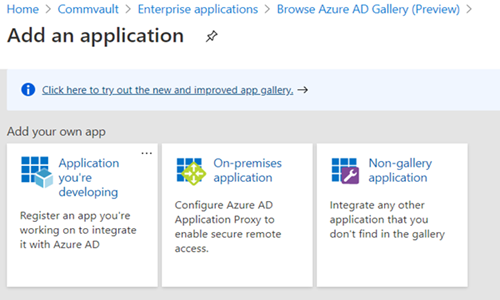
- Under Add an application, click the Non-gallery application tile.
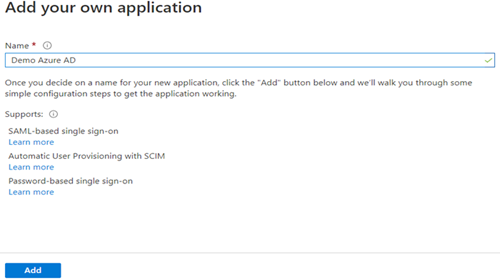
- Enter a name for the application, and then click Add.
- Review the overview, and under the Getting Started section, complete the following steps required by Microsoft: Assign users and groups and Add user.
Note: The users and groups that are assigned in the steps can only access the application. - From the navigation pane, click Single sign-on, and then click the SAML tile.
The SAML-based Sign-on page appears. - In the Basic SAML Configuration section, click Edit at the top-right corner, then in the Identifier (Entity ID) box and the Reply URL (Assertion Consumer Service URL) box, enter the Web Console URL, and then click Save.
For example, the URL should be in the following format:https://mycompany:443/webconsole.
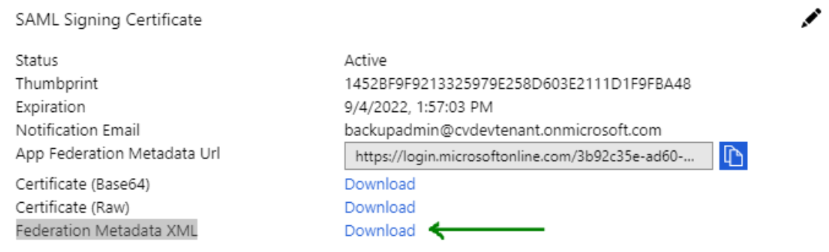
- Under the User Attributes & Claims section, click Edit at the top-right corner, then in the Unique User Identifier box, specify user.userprincipalname.
- In the SAML Signing Certificate section, next to Federation Metadata XML, click the Download link.
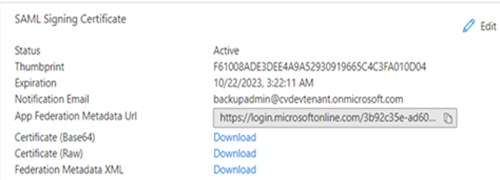
The federated metadata file that you download is the IdP metadata file that you will upload to Metallic. - Remain on the SAML-based Sign-on page.
The SP metadata file that you will create in Metallic must be uploaded to your Azure application from the SAML-based Sign-on page.
Step 2: Adding a SAML Application in Metallic
- From the navigation pane, go to Manage > Security > Identity server.
The Identity servers page appears. - In the upper-right corner of the page, click Add.
The Add domain dialog box appears. - Click SAML.
- In the Domain name box, enter a domain name to which you want users to associate with.
Note: SAML application is created using the domain name. - In the SMTP address box, enter the SMTP address of the users.
For example, if the username is jdoe@gmail.com, enter gmail.com as the SMTP address.
Note:- You can enter multiple SMTP addresses separated by a comma.
- Only users with specified SMTP addresses will be able to log in using this app.
- Upload the IdP metadata:
- Next to the Upload IDP metadata box, click Browse.
- Browse to the location of the XML file that contains the IdP metadata, select the file, and then click Open.
- Review the value in the Webconsole url box.
This value is automatically generated and is used in the SP metadata file. The format of the value ishttps://mycompany:443/webconsole.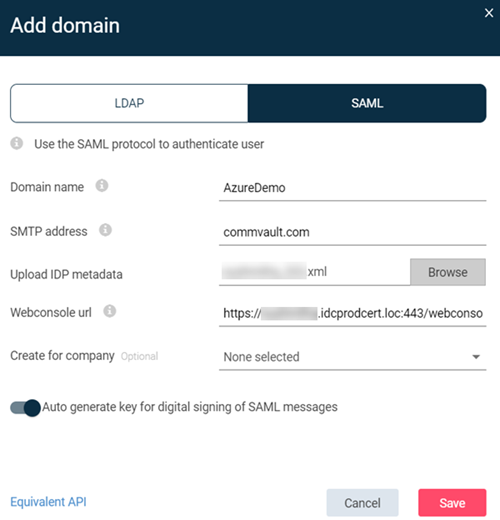
- To digitally sign the SAML message, move the Auto generate key for digital signing of SAML messages toggle key to the right.
- Click Save.
The SP metadata file is generated and the IdP metadata is saved, and the Identity servers page appears. - In the upper-right corner of the page, click Download SP metadata.
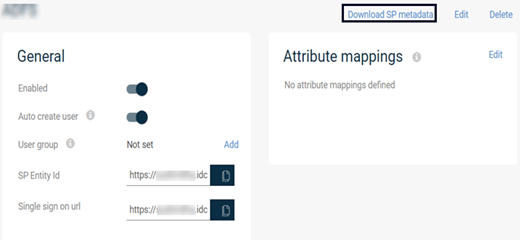
The name of the file that is downloaded begins with SPMetadata. The SP metadata file must be uploaded to the Azure application.
Step 3: Uploading the Metadata to the Azure Portal
- In the Microsoft Azure portal, on the Single sign-on page, click Upload metadata file.
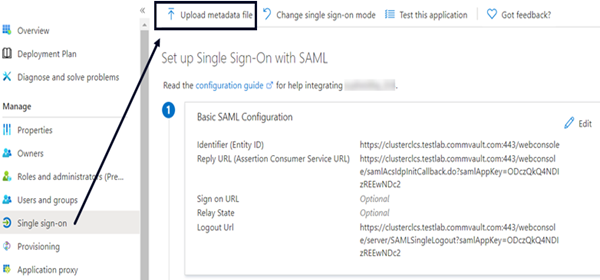
- Upload the SP metadata file.
- Click Add.
The Identifier (Entity ID), Reply URL (Assertion Consumer Service URL), and Logout URL values are pre-filled using the SP metadata file. - Click Save.
Using Okta as Your Identity Provider
Okta is a third-party identity provider (IdP) that can act as the IdP when your users log on to Metallic. Metallic is the service provider (SP).
To integrate with Okta, add a SAML application in your Okta account and in Command Center. Metadata from the Okta application (IdP) is shared with the Command Center application (SP) during this process.
Step 1: Creating an Application in Okta
- Log on to your Okta account. You will create a new application using SAML 2.0 as the sign on method.
- Follow the wizard for the general settings.
- Under Configure SAML > SAML Settings, in the Single sign on URL box and the Audience URI (SP Entity ID) box, enter the URL for the Web Console using the following format: https://mycompany:443/webconsole.
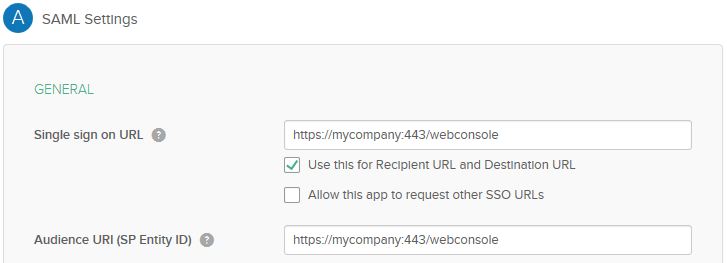
- From the Name ID format list, select Email Address.
- Continue to follow the wizard and accept the default values.
- Click Finish.
- Open the application, and then click Sign On.
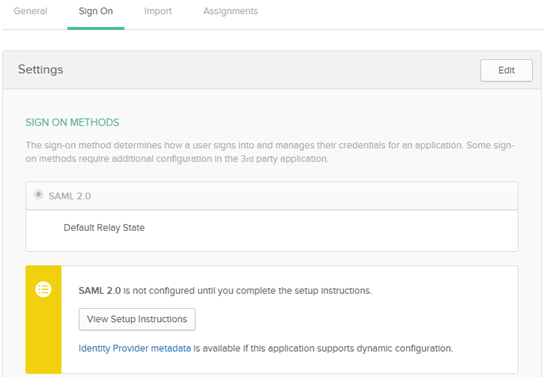
- Under the View Setup Instructions button, click Identity Provider metadata, and then save the IdP metadata file as an XML file.
The identity provider metadata file that you save is the IdP metadata file that you will upload to Metallic. - Keep your Okta account open.
The value in the Single sign on URL box in Okta must be updated after a new URL is created in Metallic.
Step 2: Adding a SAML Application in Metallic
- In the upper-right corner of the page, click Add. The Add domain dialog box appears.
- Click SAML.
- In the Domain name box, enter an application name.
- In the SMTP address box, enter the SMTP address.
- Upload the IdP metadata:
- Next to the Upload IDP metadata box, click Browse.
- Browse to the location of the XML file that contains the IdP metadata, select the file, and then click Open.
- Review the value in the Webconsole url box. This value is automatically generated and is used in the SP metadata file. The format of the value is
https://mycompany:443/webconsole. - To digitally sign the SAML message, move the Auto generate key for digital signing of SAML messages toggle key to the right.
- Click Save. The Identity servers page appears.
- In the Name column, click the identity server. The identity server properties page appears.
- In the General section, copy the value in the Single sign on url box. This value must be updated in Okta.
Step 3: Update the Single Sign-on URL in Okta
- In your Okta account, under Configure SAML > SAML Settings, in the Single sign on URL box, paste the URL that you copied from Command Center. This is the value from the Single sign on url box.
Step 4: Optional Okta Configurations
- To configure single logout in Okta, complete the following steps:
- From the generated SP metadata XML file, copy the following information:
- SP EntityId
- SingleLogoutService location with POST binding
- To download the signature certificate, log on to Command Center, and then in your web browser, type the SAML App URL in the following format: https://webconsole_hostname/adminconsole/downloadSPCertificate.do?appName=URL encoded SAML app name Example: https://company.com/adminconsole/downloadSPCertificate.do?appName=app%20Name
- Press Enter.
- In your Okta account, under General > Advanced Settings, select the Enable Single Logout box.
- In the Single Logout URL box, type the SingleLogoutService location that you copied from the SP metadata XML file.
- In the SPIssuer box, type the entityID that you copied from the SP metadata XML file.
- In the Signature Certificate box, upload the certificate that you downloaded from the SAML app URL.
- From the generated SP metadata XML file, copy the following information:
- To assign other Okta users access to your Okta account, complete the following steps:
- In your Okta account, under Assignments, click Assign, and then select one of the following options:
- To assign individual Okta users, click Assign to People.
- To assign a user group, click Assign to Groups.
- Select the user or group that you want to assign, and then click Add.
- In your Okta account, under Assignments, click Assign, and then select one of the following options:
- To assign domain users based on Okta’s user groups SAML attribute, complete the following steps:
- In your Okta account, under Group Attribute Statements, click Add.
- In the Name box, type user_groups.
- In the Filter box, assign filters as required. For example, to assign users from a user group name that starts with “domain users”, select Starts With, and then type domain users.
- Preview the SAML assertion and verify that your IdP response XML includes the user group attribute. For example: <saml2:Attribute Name=”user_groups” NameFormat=”urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified”>
<saml2:AttributeValue
xmlns:xs=”http://www.w3.org/2001/XMLSchema”
xmlns:xsi=”http://www.w3.org/2001/XMLSchema-instance” xsi:type=”xs:string”>GroupName Match Starts with “domain users” (ignores case)
</saml2:AttributeValue>
</saml2:Attribute> - In Command Center, map Okta’s user_group SAML attribute with the user group user attribute.
Usage and Metering
Billing calculations can be based on the amount of data you back up, the number of users in your environment, and the amount of Metallic Cloud storage that you use.
Total usage for a period is defined as the total cumulative count of unique entities (as defined by a globally unique identifier) protected, in any capacity and for any duration, at any point during the billing period of measurement. It is the cumulative sum of all unique entities protected throughout that billing period.
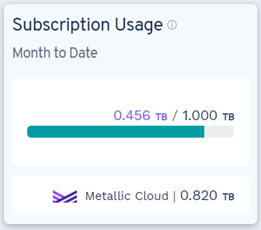
You can view usage and metering information in the Subscription Usage tile on the Hub for each type of entity:
- Metallic Cloud Storage: The peak volume of data protected in terabytes from the start of the current month to today. For more information, see Data stored in the Metallic cloud.
- VM and Kubernetes: The total number of unique virtual machines protected from the start of the current month until today. For more information, see Subscription Usage for VMs and Kubernetes.
- Files and Objects: The peak front-end size for file and object data protected from the start of the current month until today. For more information, see Subscription Usage for Files and Objects.
- Databases: The peak front-end size for database data protected from the start of the current month until today. For more information, see Subscription Usage for Databases.
- Office 365: The total number of unique users protected from the start of the current month until today. For more information, see Subscription Usage for Office 365.
- Endpoint: The total number of unique users protected from the start of the current month until today. For more information, see Subscription Usage for Endpoint.
Security and compliance
Metallic is committed to ensuring the security of your data at every level. Metallic is built on Microsoft Azure, the cloud platform leading the industry in compliance with over 90 certifications.
Commvault Systems, Inc. is also an ISO.IEC 27001:2013 certified provider whose Information Security Management System (ISMS) has received third-party accreditation from the International Standards Organization. The scope of our ISO/IEC 27001:2013 certification includes the Commvault offering Metallic.
A-lign, an independent, third-party auditor, found Metallic to have technical controls in place and formalized IT Security policies and procedures. A-lign is an ISO / IEC 27001 certification body accredited by the ANSI-ASQ National Accreditation Board (ANAB) to perform ISMS 27001 certifications.


GDPR
Metallic supports our customers’ compliance with the General Data Protection Regulation (GDPR). For information about Metallic and GDPR compliance, see GDPR readiness with Metallic.
Metallic storage
All about storage
Deciding where to store your data doesn’t have to be hard. You can choose to back up to an on-premises server, to the cloud, or to a combination of both.
Let’s look at the benefits and considerations for all of the options.
On-premises storage
Restoring data from an on-premises server is as fast as your own network.
Benefits of on-premises storage:
- Fast recovery
- No charge for moving data
- You know exactly where your data is
Considerations for on-premises storage:
- You must manage your storage infrastructure
- Adding or upgrading storage requires planning and money
Cloud storage
Storing data in the cloud gives you the flexibility to scale up or down depending on your storage needs.
Benefits of cloud storage:
- Easy to scale
- No infrastructure management
Considerations for cloud storage:
- Slower recovery
- Depending on the agreement with the cloud provider, there could be charges associated with restoring data
Related topics
Cloud storage requirements
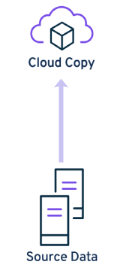
To store data in a cloud, use your own cloud or use the Metallic cloud.
Data flow
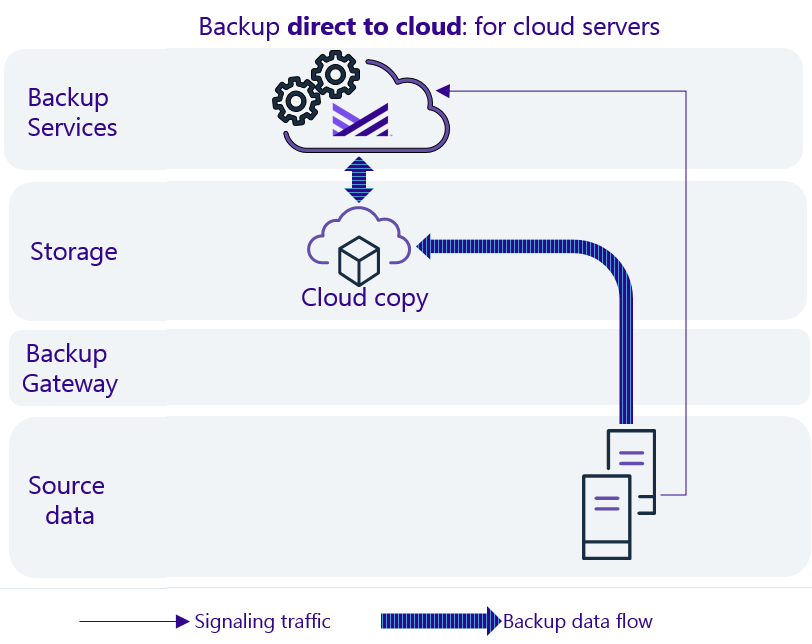
Supported providers
The following clouds are supported:
- AWS
- Azure
Data stored in the Metallic cloud
From the Hub, you can track the amount of data stored in your Metallic Azure cloud.
Usage information is available in the following tiles:
- Subscription Usage: Displays the peak volume of data protected in terabytes from the start of the current month to today in the Metallic Cloud section of the Subscription Usage tile. For usage reconciliation purposes, the peak usage value for the month is used.
- Backup Storage Used: Displays the current storage usage in terabytes. The usage includes deduplicated data and data compression. This value can vary from the peak usage value displayed in the subscription tile.
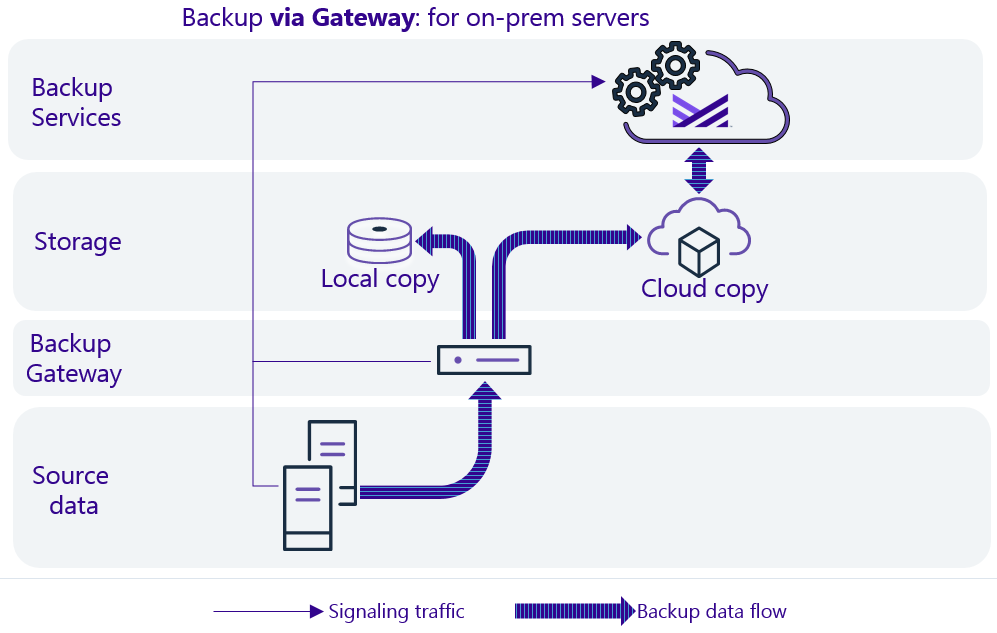
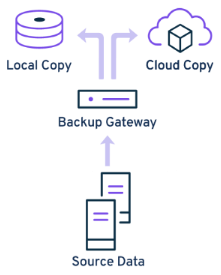
Metallic backup gateway requirements
The on-premises backup gateway functions as a gateway between the on-premises data source and the cloud backup service. If you want to use on-premises backup storage, you can store a copy of your data on the on-premises backup gateway.
Important: The on-premises backup gateway must be able to connect to the Metallic Backup Service and must be able to access the servers that need to be backed up.
Data flow
Hardware requirements
Install the backup gateway package on a server that meets the following minimum requirements.
| Requirements | 1TB/10VMs | 3TB/30VMs | 10TB/100VMs | 30TB/300VMs |
|---|---|---|---|---|
| CPU | 2 vCPUs | 2 vCPUs | 2 vCPUs | 4 vCPUs |
| RAM | 8 GB | 16 GB | 16 GB | 32 GB |
| Disk: Operating system and program files | 300 GB, 200 IOPS | 500 GB, 250 IOPS | 1 TB, 250 IOPS | 3 TB, 500 IOPS |
| Disk: On-premises copy (30 days retention maximum) | 2 TB, any IOPS | 6 TB, any IOPS | 20 TB, any IOPS | 60 TB, any IOPS |
Network requirements
- TCP 443 outbound must be open for network access to backup service hosts and storage services (*.metallic.io).
- To back up VMware servers, the backup gateway must be able to access the VMware environment and components:
- vCenter: Port for web service (default: 443) must be opened. If vCenter is configured to use non-default ports, the non-default ports must also be opened.
- ESX Server: Ports for web service (default: 443) and TCP/IP (default: 902) must be opened for the vStorage APIs for data protection.
- To back up Hyper-V virtual machines (VMs), the Metallic VM proxy must be able to access the backup gateway on the port for the web service (default: 443).
Sizing
| Requirements | 1TB/10VMs | 3TB/30VMs | 10TB/100VMs | 30TB/300VMs |
|---|---|---|---|---|
| Network interface card | 1 Gbps NIC | 1 Gbps NIC | 10 Gbps NIC | 2 10 Gbps NIC |
| Available internet bandwidth requirements | 30 Mbps | 100 Mbps | 1 Gbps | 3 Gbps |
Supported operating systems
The following operating systems are supported:
- Microsoft Windows Server 2019 Editions
- Microsoft Windows Server 2012 R2 Editions
- Microsoft Windows Server 2012 Editions
- Microsoft Windows Server 2016 Editions
- Microsoft Windows Client 10 Editions
VM & Kubernetes
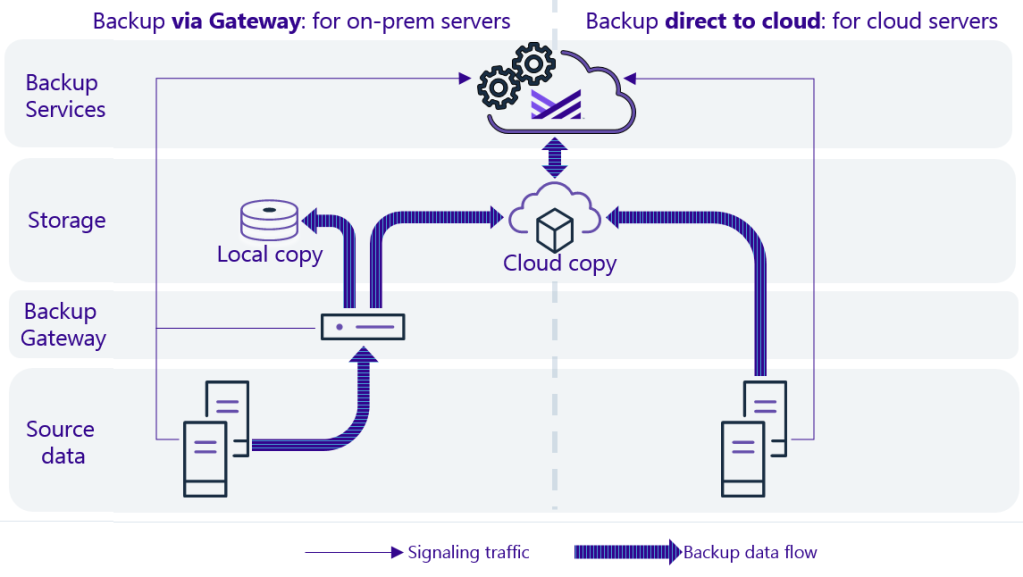
To store data in a cloud, use your own cloud or use the Metallic cloud. To store data on-premises, configure a backup gateway. Data can be stored directly on the backup gateway, or you can access other resources by using a UNC path.
Flow
Subscription Usage for VMs and Kubernetes
You can view usage and metering information in the Subscription Usage tile and the Subscription Usage report on the Hub.
Subscription Usage Tile
The Subscription Usage tile in the Hub displays the total number of unique virtual machines protected from the start of the current month until today.
If a VM was protected for one or more days in the month, the VM is counted as part of the total VM usage. The VM is counted even if it is removed from a backup schedule or if backup data was deleted from the system. If the VM is not backed up in the following months, it is not counted as part of subscription usage for those months.
For example, if VM01 and VM02 are protected on the first day of the month, and VM01 is removed from the system later that month, the total number of VMs protected in the month is two VMs. If VM01 is not backed up in the following month and VM02 is backed up, the total number of VMs protected in the month is one VM.
Subscription Usage Report
To access the Subscription Usage report, click the link in the Subscription Usage tile in the Hub. The Subscription Usage report lists the names of all the VMs protected from the start of the current month to today. Use this report to validate the subscription usage you are charged for.
Microsoft Azure VM
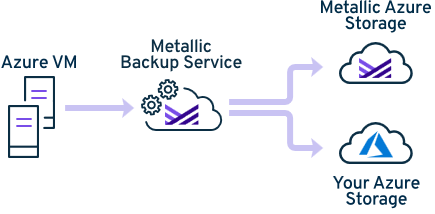
You can use Metallic to back up and to restore Azure virtual machines (VMs) residing in Azure public cloud datacenters. Metallic backups leverage Azure snapshots and Metallic streaming backups.
To allow Metallic backup services to connect to and to back up your Azure VMs, you must set up an application and tenant in the Azure portal.
Data Flow
Setting Up an Application and Tenant for Azure Resource Manager
To create an Azure virtualization client in the Metallic software, you need to set up an application and tenant for the Azure Resource Manager.
An application is a specific cloud service associated with your Azure account, and the tenant is a client or organization that manages an instance of the cloud service. The application and tenant are associated with your subscription through Azure Active Directory, which provides identity and access management for the Azure cloud.
To complete the setup of the Azure virtualization client in the Metallic software, you need the following:
- Application name
- Application ID
- Subscription ID
- Tenant ID (Directory ID)
- Application key
Before You Begin
Collect the following information for your Azure account:
- Subscription ID for the Azure account
- User credentials with Service Administrator capabilities, for logging in to your Azure account
Procedure
- Log on to the public Azure portal with service administrator credentials.
- From the All services menu, select the App registrations tab, and then click on New registration.
- Enter the appropriate values for the following:
- Name: Name of the application to be created on Azure Active Directory.
- Account type: Select one from the following:
- Accounts in this organizational directory only
- Accounts in any organizational directory
- Accounts in any organizational directory and personal Microsoft accounts.
- Redirect URI: Optional. https://app_name (URL including the application name you specify). For example: MyWebApp and https://MyWebApp.
- Click Register.
The application will be listed on the App Registration tab. Note down the Application ID. - Go to the API permissions blade.
- Click Add a permission to add the required API permissions:
- Select the Microsoft API: Azure Service Management.
- Select the option to provide delegated permissions to Access Azure Service Management as organization users.
- Click Add permissions.
Note: If you are configuring a Linux proxy, you must also request API permissions for the Microsoft API: Azure Storage.
- Go to the Certificates & secrets blade.
- Click on New client secret, and then provide the key description and expiration date.
- Click Save.
A unique secret key is generated for the application.
Important: Save the key value. The key value will be your application password. You will not be able to retrieve the key after you leave the Certificate & secrets tab/blade. - From the All services menu, click the Subscriptions tab, and then select the subscription ID for which the virtualization client needs to be created.
- To define a custom role instead of using the predefined Contributor role, do the following:
Define a custom role to specify more limited permissions that can be used for backup and restore operations, either for a specific resource group or for the subscription as a whole.- Download the CVBackupRole.json file, which contains the minimum permissions needed for Azure backup and restore operations.
- Use a JSON editor to modify the following entry and change #SubscriptionID# to your subscription ID: “AssignableScopes” : [“/subscriptions/#SubscriptionID#“]
- To create a custom role, refer to Custom roles for Azure resources.
- On the Access Control (IAM) tab, click Add to add a service principal user.
- On the Add Permissions blade, select the Contributor role or the custom role that you created.
- Select Azure AD user, group, or application.
- In the Select field, type the application name, and then select the application created in previous step.
- You can obtain the Tenant ID from the public Azure cloud by selecting Azure Active Directory > Properties > Directory ID.
The Directory ID is also the Tenant ID.
What to do next
In the Metallic software, create the Azure virtualization client using the Subscription ID, Tenant ID, Application ID, and Application Key.
Accessing the virtual machine overview
To perform operations on your Azure VMs, open the virtual machine overview page.
Procedure
- Go to the Hub.
- On the Core tab, in the Protected Data Sources tile, above Virtual Machines, click the number.
The Virtual machines page appears.
- In the Name column, click the virtual machine that you want to open.
Kubernetes
You can use Metallic to back up and restore stateful Kubernetes applications and data.
Backups
Metallic provides the following key backup capabilities:
- Automatic discovery and backup of applications by using label selectors.
- Automatic discovery and backup of namespaces.
- Back up any Kubernetes orchestrated cluster, on-premise or cloud (such as GCP, AWS), and managed Kubernetes PaaS offerings such as Amazon Elastic Kubernetes Service (EKS) and Azure Kubernetes Service (AKS).
- Back up Kubernetes applications. An application can be a pod, a deployment, a StatefulSet, or a workload.
- Back up persistent volumes and persistent volume claims.
- Back up custom resource definitions (CRD).
Restores
Restores You Can Perform
- Recover a complete application to a previous point in time, including auto deployment to a new application or a new cluster.
- Recover a sub-application from a composite (custom resource) application.
- Recover an individual data volume from an application, for attaching to a new application.
- Recover or download files and folders from data volumes, or application YAML manifests.
Granularity You Can Use for Restores
- Application and data
- Data volumes
- Data (folders and files) from within the volume.
Backups You Can Use for Restores
- Backups from any date/time, including the most recent backup
Destinations You Can Restore To
- The current volume, application, or cluster (in place)
- A different volume, application, or cluster (out of place)
Kubernetes Backup Requirements
Verify that your environment meets the requirements for Kubernetes.
Infrastructure
Metallic supports Kubernetes backups via a backup gateway or via Microsoft Azure Kubernetes Service (AKS).
Metallic Backup Gateway
Ensure that the following infrastructure requirements are met:
- At least one Windows host (called an access node) that can communicate with the Kubernetes cluster.
- The access node must have the Virtual Server Agent (VSA) package installed. For information about the access node software and hardware specifications, see “Access Node Software” and “Access Node Hardware”, below.
Microsoft AKS
You can use Microsoft AKS to back up Kubernetes.
There are no infrastructure requirements to use Microsoft AKS.
Access to Kubernetes Cluster
Ensure that the following requirements are met:
- Kubernetes cluster with access to the kube-apiserver endpoint (for example, https://kube-apiserver:kube-apiserver_port_number). The default API port is 6443.
- A Kubernetes service account or an account to access Kubernetes.
External Connectivity
Ensure that the Kubernetes cluster can access the Docker Hub (https://hub.docker.com) so that it can download the following docker image: https://hub.docker.com/_/debian.
Note: Metallic downloads and uses the debian:stretch-slim image to create a temporary container during backups.
Kubernetes Distribution
Any CNCF-certified Kubernetes distribution version 1.18, 1.17, 1.16, 1.15 or 1.14.
For a list of CNCF-certified Kubernetes distributions, see CNCF-certified Kubernetes distribution.
The following distributions are validated by Metallic:
- Red Hat OpenShift 4.5, 4.4, 4.3, 4.2, and 4.1
- Azure Kubernetes Service (AKS)
- Amazon Elastic Kubernetes Service (EKS)
Access Node Software
The access node can run the following Windows operating systems:
- Microsoft Windows Server 2019 Editions
- Microsoft Windows Server 2016 Editions
- Microsoft Windows Server 2012 R2 Editions
Access Node Hardware
For faster backups and restores, you can install multiple access nodes.
Ensure that each access node meets the following minimum hardware specifications:
- 2 x vCPUs
- 4 GB RAM
- 100 MB of local disk space for the Commvault software
- 1GbE network interface for backup data
Kubernetes Backup Guided Setup
You can follow a guided setup for Kubernetes backup. The setup creates a cluster configuration and enables the Kubernetes solution.
For more information, see the following:
- Kubernetes Backup Across a Local Network Via a Backup Gateway
- Kubernetes Backup Directly to the Azure Kubernetes Service (AKS)
Guided Setup – Kubernetes Backup Across a Local Network Via a Backup Gateway
You can follow a guided setup for Kubernetes backup across a local network via a backup gateway. The setup creates a cluster configuration and enables the Kubernetes solution.
Before You Begin
Ensure that at least one Linux or Windows host can communicate with the Kubernetes cluster. The host must have the Virtual Server Agent (VSA) package installed.
Procedure
- Go to the Hub.
- On the Compute tab, select New configuration > Kubernetes.
The How do you want to deploy your backup? page appears.
- Select Backup via Gateway and then click Next.
The Select backup gateway page appears.
- Follow the instructions on the page to download and install the software on the backup gateway.
- Enter the hostname for the backup gateway.
- Click Next.
The Configure a local backup target for quick restores page appears.
- Follow the instructions on the page to add a new local storage location.
- Optional: Select Backup directly to cloud without a local backup target.
The Configure cloud backup storage page appears.
- In the Storage account list, select your storage account.
- In the Cloud storage provider list, select your Cloud storage provider.
- In the Storage region list, select your storage region.
- In the New storage location name field, enter a name for your storage location.
- In the Account name field, enter the email address of your account.
- In the Access key ID field, enter your access key ID.
- In the Container field, select a container.
- Click Create.
- Click Next.
The Create a plan page appears.
- Select a retention plan from the options on the page.
- In the New plan name field, enter a plan name.
- Click Create.
- Click Next.
The Add cluster page appears.
- In the API server endpoint field, enter the API server endpoint URL.
Typically, the URL is https://kube-apiserver:kube-apiserver_port_number. If you do not know the URL, you can use the kubectl config view.
- In the Name field, enter a name for the cluster.
- In the Authentication list, select the authentication method as follows:
- Service account: Enter the Kubernetes service account name, and then copy the token into the Service token box.
A Kubernetes service account that is used to access Kubernetes must have the cluster admin role assigned.
- Kubeconfig file: Select the configuration file.
- User name and password: Enter the user name and password.
- Service account: Enter the Kubernetes service account name, and then copy the token into the Service token box.
- Click Next.
- The Add application group page appears.
- In the Cluster list, select a cluster.
- In the Name field, enter a name for the application group.
- Browse for and then select the applications to back up.
- Click Save.
Guided Setup – Kubernetes Backup Directly to the Azure Kubernetes Service (AKS)
You can follow a guided setup for Kubernetes backup directly to the Azure Kubernetes Service (AKS).
Before You Begin
Ensure that at least one Linux or Windows host can communicate with the Kubernetes cluster. The host must have the Virtual Server Agent (VSA) package installed.
Procedure
- Go to the Hub.
- On the Compute tab, select New configuration > Kubernetes.
The How do you want to deploy your backup? page appears.
- Select Azure AKS.
The Configure cloud backup storage page appears.
- In the Storage account list, select your storage account.
- In the Cloud storage provider list, Microsoft Azure storage is selected.
- In the Storage region list, select your storage region.
- In the New storage location name field, enter a name for your storage location.
- In the Account name field, enter the email address of your account.
- In the Access key ID field, enter your access key ID.
- In the Container field, select a container.
- Click Create.
- Click Next.
The Create a plan page appears.
- Select a retention plan from the options on the page.
- In the New plan name field, enter a plan name.
- Click Create.
- Click Next.
The Add cluster page appears.
- In the API server endpoint field, enter the API server endpoint URL.
Typically, the URL is https://kube-apiserver:kube-apiserver_port_number. If you do not know the URL, you can use the kubectl config view.
- In the Name field, enter a name for the cluster.
- In the Authentication field, select the authentication method as follows:
- Service account: Enter the Kubernetes service account name, and then copy the token into the Service token box.
A Kubernetes service account that is used to access Kubernetes must have the cluster admin role assigned.
- Kubeconfig file: Select the configuration file.
- User name and password: Enter the user name and password.
- Service account: Enter the Kubernetes service account name, and then copy the token into the Service token box.
- Click Next.
The Add application group page appears.
- In the Cluster list, select a cluster.
- In the Name field, enter a name for the application group.
- Browse for and then select the applications to back up.
- Click Save.
Kubernetes Restores
You can restore the applications and data in a Kubernetes cluster to its current location (in place), to a different cluster (out of place)
Types of Restore You Can Perform
- Application restore
- Volume and data restore
- Application manifest restore
Restore Kubernetes Applications
You can restore the Kubernetes applications in-place or out-of-place.
Restoring Kubernetes Applications In Place
You can restore Kubernetes applications in place.
Procedure
- From the navigation pane, go to Protect > Kubernetes.
The Clusters page appears.
- In the Name column, click the cluster.
The cluster page appears.
- Under Application groups, in the row for the application group that you want to restore, click the action button, and then click Restore.
The Select restore type page appears.
- Click Full application.
The Restore page appears.
- Select the applications to restore.
- To restore from a specific copy of backup data, in the upper-right corner of the page, from the Restore from default copy list, select the copy.
If you select Restore from default copy (default), the restore operation searches for the requested data in the primary copy, and automatically selects a different copy if the data is not found in the primary copy.
- Click Restore.
The Restore options dialog box appears.
- From the Access node list, select the access node.
- Click Submit.
Restoring Kubernetes Applications Out of Place
You can use out-of-place restores to migrate Kubernetes applications and data across cloud providers, from on-premise to cloud, or from cloud to on-premise.
You can perform out-of-place restores to any Kubernetes cluster, for example:
- To a different cluster
- From on-premise to a cloud GKE
- From GKE to EKS
- From EKS to on-premise
Out-of-place restores allow you to configure a different storage class that will be used to provision the data volumes. Storage classes abstract the underlying physical storage tier used by the Kubernetes cluster. With this approach, the development and test restores of production data do not incur the cost of primary production storage.
Procedure
- From the navigation pane, go to Protect > Kubernetes.
The Clusters page appears.
- In the Name column, click the cluster.
The cluster page appears.
- Under Application groups, in the row for the application group that you want to restore, click the action button, and then click Restore.
The Select restore type page appears.
- Click Full application.
The Restore page appears.
- Select the applications to restore.
- Click Restore.
The Restore options dialog box appears.
- Click Out of place.
- Click Submit.
Restore Kubernetes Volume and Data
You can restore the Kubernetes volumes and data in-place or out-of-place.
Restoring Kubernetes Volumes and Data In Place
You can restore the Kubernetes data volumes or specific files and folders in place.
Procedure
- From the navigation pane, go to Protect > Kubernetes.
The Clusters page appears.
- In the Name column, click the cluster.
The cluster page appears.
- Under Application groups, in the Actions column for the application group, click the action button, and then click Restore.
The Select restore type page appears.
- Click Volumes and data.
The Restore page appears.
- Select the volumes or specific files and folders to restore.
- To restore from a specific copy of backup data, in the upper-right corner of the page, from the Restore from default copy list, select the copy.
If you select Restore from default copy (default), the restore operation searches for the requested data in the primary copy, and automatically selects a different copy if the data is not found in the primary copy.
- Click Restore.
The Restore options dialog box appears.
- Click In place.
- Click Submit.
Restoring Kubernetes Volumes and Data Out of Place
You can restore the Kubernetes data volumes or specific files and folders out of place.
Note: For OpenShift, verify that the applications are not running when you perform a restore to a PVC.
Procedure
- From the navigation pane, go to Protect > Kubernetes.
The Clusters page appears.
- In the Name column, click the cluster.
The cluster page appears.
- Under Application groups, in the Actions column for the application group, click the action button, and then click Restore.
The Select restore type page appears.
- Click Volumes and data.
The Restore page appears.
- Select the volumes or specific files and folders to restore.
- To restore from a specific copy of backup data, in the upper-right corner of the page, from the Restore from default copy list, select the copy.
If you select Restore from default copy (default), the restore operation searches for the requested data in the primary copy, and automatically selects a different copy if the data is not found in the primary copy.
- Click Restore.
The Restore options dialog box appears.
- Click In place.
- Click Submit.
Restore Kubernetes Application Manifests
You can restore the Kubernetes application manifests to a specific path on the access node.
You can restore Kubernetes configurations by using the manifest YAML files. A YAML file is used to store or transfer application configurations between applications.
Restoring Kubernetes Application Manifests
From a YAML file, you can restore the Kubernetes data volumes or specific files and folders, to a specific path on the access node.
Procedure
- From the navigation pane, go to Protect > Kubernetes.
The Clusters page appears.
- In the Name column, click the cluster.
The cluster page appears.
- Under Application groups, in the Actions column for the application group, click the action button, and then click Restore.
The Select restore type page appears.
- Click Application manifests.
The Restore page appears.
- Select the YAML file to restore.
- Click Restore.
The Restore options dialog box appears.
- From the Access node list, select an access node to stage the data for the restore operation.
- To use a saved user credentials to access data, enable the Impersonate user slider, and then select the credential to use.
- In the Path box, type the full path to the destination folder.
- To overwrite the existing data, move the Unconditionally overwrite if it already exists toggle key to the right.
- Click Submit.
Application Consistent Protection for Kubernetes
For Kubernetes, you can add pre-process script files or post-process script files on both Windows and Linux access nodes.
Pre-scripts and post-scripts are batch files or shell scripts that you can run before or after certain job phases. Both pre-script and post-script must be provided for application consistent protection.
Migration Use Cases for Kubernetes
You can use backups and restores to migrate Kubernetes data and applications.
Application Migration Using Out-of-Place Restores
You can use out-of-place restores to migrate applications as follows:
- From on-premise clusters to cloud-managed clusters (for example, AKS, GKE, or EKS)
- From one one cloud-managed cluster to another cloud provider (for example, between AWS, Azure, and Google Cloud Platform)
- From a cloud-managed cluster to a cloud IaaS cluster (for example, from GKE/EKS/AKS to AWS EC2, Azure, or Google VM instances)
Data Migration Using Backups
You can use application backups or volume backups to migrate data. You can use backups to migrate data across cloud providers, from on-premise to cloud, and from cloud to on-premise.
Related Topics
Restoring Kubernetes Applications Out of Place
Requirements for backing up Hyper-V servers
Review the following requirements if you want to back up on-premises Hyper-V servers.
To backup on-premises data, a backup gateway is required. To review the requirements for the backup gateway, see Backup gateway requirements.
Hyper-V deployment model
To back up Hyper-V virtual machines (VMs), Metallic VM proxy for Hyper-V must be installed on each Hyper-V host in the cluster. The Metallic VM proxy for Hyper-V communicates on TCP port 443 with the Metallic backup services hosted in the cloud and with the Metallic backup gateway.
Best Practice: Install the Metallic VM proxy for Hyper-V and the Metallic backup gateway on the same local network for the best backup and recovery performance. Using this configuration, options for both local and cloud backup copies are available.
Authenticating to Hyper-V
- Obtain the user credentials to access the Hyper-V server from your Hyper-V administrator. The user must be part of the following administrator groups on the Hyper-V host:
- Local Administrators group (for Hyper-V Server 2008 R2 and Hyper-V Server 2016)
- Any user that are part of Hyper-V Administrators group (for Hyper-V Server 2012 and 2012 R2)
Physical machine operating systems
- Microsoft Windows Server 2019 (including Core Edition)
- Microsoft Hyper-V Server 2019 (including Core Edition)
- Microsoft Windows Server, version 1709 (including Core Edition)
- Microsoft Hyper-V Server, version 1709 (including Core Edition)
- Microsoft Windows Server 2016 (including Core Edition)
- Microsoft Hyper-V Server 2016 (including Core Edition)
- Microsoft Windows Server 2012 R2 (including Core Edition)
- Microsoft Hyper-V Server 2012 R2 (including Core Edition)
- Microsoft Windows Server 2012 (including Core Edition)
- Microsoft Hyper-V Server 2012 (including Core Edition)
- Microsoft Windows Server 2008 R2 SP1
Virtual machine operating systems
All guest operating systems supported by Microsoft Hyper-V.
Hyper-V integration services
To back up the virtual machines on a Hyper-V server or cluster, Hyper-V integration services must be installed and updated on the virtual machine.
Hard drive
100 GB is recommended.
Allocation unit size of the NTFS volumes
The cluster size or the allocation unit size of an NTFS volume in a virtual machine must be multiple of 1024 bytes. You can set the cluster size before formatting a volume. The default cluster size is 4096 bytes.
Microsoft Visual C++
The following Redistributable Package is installed automatically. The Redistributable Package can co-exist with other versions of this software.
- Microsoft Visual C++ 2010 Redistributable Package
- Microsoft Visual C++ 2013 Redistributable Package
- Microsoft Visual C++ 2017 Redistributable Package
Disclaimer
Third-party maintenance (minor) releases or service packs that are supported by the Commvault software may not be listed in our System Requirements. When possible, Commvault provides information on any known issues related to these minor releases or service packs. In some cases, these minor releases or service packs affect how the Commvault software works. Commvault software may experience changes in functionality as the result of the third-party minor release or service pack. These changes are beyond the control of Commvault. Platforms that are supported in the current version of Commvault software may not be supported in earlier versions of the software. Contact your software provider to ensure that third-party minor releases or service packs are compatible with the Commvault software.
Additional considerations regarding minimum requirements and End-of-Life policies from third-party vendors also apply.
Requirements for backing up VMware servers
Review the following requirements if you want to back up on-premises VMware servers.
To backup on-premises data, a backup gateway is required. To review the requirements for the backup gateway, see Backup gateway requirements.
VMware vCenter Server Support
The following versions are supported for vCenter Server and vCenter Server Appliance. vCenter Server support includes support for vSphere, Virtual Disk Development Kit (VDDK), ESX or ESXi, and file system versions as provided by the vCenter version.
For more information, see Correlating build numbers and versions of VMware products (1014508).
As a general rule of thumb, each version of the VDDK supports vCenter Server for the two previous major versions and for the next minor version. For example, VDDK 6.0.0 can be used with vCenter Server 5.5, 5.1, or 6.0 Update 1.
When VMware issues new versions or updates, Metallic tests against the current service pack before announcing support. For new VMware versions or updates released between Metallic service packs, and for earlier supported versions or service packs, Metallic provides continuing support, including Hot Fixes as needed to address VMware changes to functions that affect backup and recovery.
vCenter Server Version
- 6.7 Update 3 (all minor updates)
- 6.7 Update 2 (all minor updates)
- 6.7 Update 1 (all minor updates)
- 6.7 (all minor updates)
- 6.5 Update 3 (all minor updates)
- 6.5 Update 2 (all minor updates)
- 6.5 Update 1 (all minor updates)
- 6.5 GA (all minor updates)
- 6.0 Update 3 (all minor updates)
- 6.0 Update 2 (all minor updates)
- 6.0 Update 1 (all minor updates)
- 6.0 GA (all minor updates)
- 5.5 Update 3 (all minor updates)
- 5.5 Update 2 (all minor updates)
- 5.5 Update 1 (all minor updates)
- 5.5 GA (all minor updates)
- 5.1 (all updates)
- 5.0 (all updates)
- 4.1 (all updates)
Note: If VMs are part of ESX 4.1, then streaming and IntelliSnap backups are supported only through the vCenter. You cannot use a standalone ESX 4.1 server.
ESX Host Support
Before configuring backup of any ESXi servers, ensure that you are using Essentials licensing level or higher. The vStorage APIs for Data Protection (VADP) are not provided with the free version of ESXi.
VDDK Support
Metallic includes the latest supported VDDK. Multiple versions of the VDDK are included, and the appropriate VDDK for the vSphere version is loaded automatically when required.
vCenter Server Versions Required for Specific Features
Some features are supported only for more recent versions of vCenter Server. The following table shows the required versions for features that are dependent on the version of vCenter Server and associated software. Support includes all updates for each major version unless an update is specifically excluded.
| Feature | Required Version of vCenterServer |
|---|---|
| Agentless file restores | 5.1, 5.5, 6.0, 6.5, 6.7 |
| File Recovery Enabler for Linux | 4.1, 5.1, 5.5, 6.0, 6.5, 6.7 |
Virtual Machine Hardware
Version 4.0, 7.0, 8.0, 9.0, 10.0, 11.0, 13.0, 14.0, 15.0
Virtual Machine Operating Systems
All Guest Operating Systems supported by VADP.
Datastore Support
- Network File System (NFS)
- Virtual Machine File System (VMFS)
- Virtual storage area network (vSAN)
- VMware Virtual Volume (VVol)
VMware Tools on Virtual Machines
The latest version of VMware Tools supported by the host should be installed on each virtual machine. At a minimum, the version of VMware tools on virtual machines must be supported on the host; unsupported versions must be upgraded. For more information about VMware Tools support for Windows and Linux guest VMs, see the VMware Compatibility Guide.
open-vm-tools
For UNIX guest VMs running the following operating system releases, open-vm-tools can be used:
- Fedora 19 and later
- Debian 7.x and later
- openSUSE 11.x and later
- Recent Ubuntu (12.04 LTS, 13.10 and later)
- Red Hat Enterprise Linux 7.0 and later
- CentOS 7.0 and later
- Oracle Linux 7.0 and later
- SUSE Linux Enterprise 12 and later
For more information, see VMware support for open-vm-tools (2073803).
Allocation Unit Size of NTFS Volumes
The cluster size or the allocation unit size of an NTFS volume in a virtual machine must be multiple of 1024 bytes per cluster. You can set the cluster size before formatting a volume. The default cluster size is 4096 bytes per cluster.
Disclaimer
Third-party maintenance (minor) releases or service packs that are supported by the Commvault software may not be listed in our System Requirements. When possible, Commvault provides information on any known issues related to these minor releases or service packs. In some cases, these minor releases or service packs affect how the Commvault software works. Commvault software may experience changes in functionality as the result of the third-party minor release or service pack. These changes are beyond the control of Commvault. Platforms that are supported in the current version of Commvault software may not be supported in earlier versions of the software. Contact your software provider to ensure that third-party minor releases or service packs are compatible with the Commvault software.
Additional considerations regarding minimum requirements and End-of-Life policies from third-party vendors also apply.
Transport Modes for VMware
By default, the transport mode is selected automatically for backups and restores, based on the gateway used and the virtual machines being backed up or restored. You can force a specific transport mode by configuring it.
The following transport modes are available in VMware. Advanced transport methods (HotAdd) replace the proxy-based VMware Consolidated Backup (VCB) solution.
- SAN (storage area network) – SAN mode is supported for directly connected storage using Fibre Channel (FC) or Internet SCSI (iSCSI) protocols. With automatic transport mode selection, SAN mode is selected if SAN storage is connected to the ESX host. The Virtual Server Agent must have access to the datastore LUNs (logical drives) that provide storage for virtual machine disks. Data is read directly from the storage where virtual machines reside, without going through the ESX host or transferring data over the local area network (LAN). The ESX host is contacted only to coordinate access to the LUN.
- HotAdd – In HotAdd mode, software is installed on a virtual machine residing on an ESX Server. The term HotAdd refers to the way the backups are completed. In HotAdd mode, virtual disks from the virtual machines being backed up are automatically mounted to the gateway, so they can be accessed by the gateway as local disks. The ESX host the gateway is running on must have access to all datastores for the virtual machine. If the virtual machine and the gateway are not on the same host, all datastores must be shared between the hosts. In vSphere 5.0, the SCSI HotAdd feature is enabled only for vSphere editions Enterprise and higher, which have Hot Add licensing enabled. No separate Hot Add license is available for purchase as an add-on. In vSphere 4.1, Hot Add was also enabled in the Advanced edition. Customers with vSphere Essentials or Standard editions are not able to perform proxy-based backup, which relies on SCSI HotAdd. Those customers must use alternate transport modes.
- Local Area Network (NBD and NBDSSL) – NBD (network block device) and NBDSSL (encrypted NBD) transmit data over the TCP/IP connection between the ESX server and the gateway computer. NBD serves as a fallback when other transport modes are not available. The local area network (LAN) can be the production network or a dedicated backup network. NBDSSL is similar to NBD mode, but data transfer between the gateway computer and the ESX server is encrypted. Encryption should be used for sensitive information, even within a private network.
SAN and HotAdd transport can enable LAN-free backups and restores. In most scenarios, backups and restores using SAN and HotAdd transport are faster than local area network (LAN) operations using network block device (NBD) or secure NBD (NBDSSL).
SAN restores using thin disk provisioning can be slower than LAN restores; performance can be improved by using NBD or by setting the transport mode to SAN and forcing the disk type to thick, which uses eager zero provisioning.
The following table summarizes the configurations based on the storage type.
| Mode | Datastore Storage Type | VM Data Protected by Single Node | Additional Comments |
|---|---|---|---|
| LAN Free SAN mode | VMFS using Fibre Channel or iSCSI | Up to 40 TB | Software installed on the same physical computer with direct connection to datastore. Eliminates data transfer over network during backup and restore. Provides best backup and restore performance. |
| LAN Free HotAdd mode | VMFS, NFS, vSAN, VVol | Up to 30 TB | Software installed on virtual machine running on host with access to datastore. Eliminates data transfer over network during backup and restore. |
| Network based (NBD, HotAdd, NAS) | VMFS, NFS, vSAN, VVol, direct attached storage | Software installed on different computers. The software writes over the network to a remote computer. Depends on infrastructure. |
Connectivity
Configure DNS on the backup gateway, ESX hosts, and vCenter Server. For any transport mode, missing or incorrect DNS configuration produces nslookup errors during fully qualified domain name (FQDN) resolution.
File & Object Storage
Subscription Usage for Files and Objects
You can view usage and metering information in the Subscription Usage tile and the Subscription Usage report on the Hub.
Subscription Usage Tile
The Subscription Usage tile in the Hub displays the peak front-end size for file and object data protected from the start of the current month until today. The front-end size is the source data capacity before compression and deduplication.
If file and object data was protected for one or more days in the month, the data is counted as part of the peak front-end size for that month. The data is counted even if it is removed from a backup schedule or if backup data was deleted from the system. If the file and object data is not backed up in the following months, it is not counted as part of subscription usage for those months.
For example, if FS01 and FS02 (each with 1 GB capacity) are protected on the first day of the month, and FS01 is removed from the system later that month, the peak front-end size protected in the month is 2 GB. If FS01 is not backed up in the following month and FS02 is backed up, the peak front-end size protected in the month is 1 GB.
Subscription Usage Report
To access the Subscription Usage report, click the link in the Subscription Usage tile in the Hub. The Subscription Usage report lists the names of all the file and object servers or instances with front-end size protected from the start of the current month to today. Use this report to validate the subscription usage you are charged for.
Files
To store data in a cloud, use your own cloud or use the Metallic cloud. To store data on-premises, configure a backup gateway. Data can be stored directly on the backup gateway, or you can access other resources by using a UNC path.
Data flow

Push installations
Applies to: Core installations for Windows, Linux, and Microsoft SQL Server
To install software on the server that you want to back up, you can push the software from the backup gateway to the server. To perform a push installation, you need the name of the server that you want to back up and the user credentials for the server.
To successfully perform a push installation, do the following:
- Verify that the backup gateway has network access to the server.
- Obtain system administrator (sysadmin) user credentials for the server.
- Windows computers: The Remote Registry service must be enabled and configured to automatically start during the computer startup.
Firewall and Network Port Requirements
Turn off the firewall services on the server, and temporarily open the following inbound network ports before performing the push installation:
- For UNIX, Linux, and Macintosh computers, enable SSH (Secure Shell), and then open port 22.
- For Windows computers, do the following:
- Open Port 135 for DCOM (Distributed Component Model).
- Open Port 139 for NetBIOS Session Service (if you are using legacy Windows computers, such as Windows NT or earlier versions).
- Open Port 445 for SMB (Server Message Block) file sharing.
- Open the Windows Management Instrumentation (WMI) port. For instructions on setting up a fixed port for WMI, see Setting Up a Fixed Port for WMI on the Microsoft website.
- Important: If Windows Firewall is enabled on the computer, do one of the following:
- Temporarily open the following ports in Windows Firewall: – Port 135 for DCOM-In (COM + Network Access) – Port 445 for SMB – WMI port
- Set up a remote cache in the network where the computer resides.
Customizing the Backup Content for a Server
You can customize the backup content for a file server.
The backup content originally comes from the plan associated with the file server. If you customize the backup content for the file server, the backup content on the plan is not affected.
The following tabs are available to add customized content:
- On the Content tab, you specify the content that you want to back up.
- On the Exceptions tab, you specify the content that you do not want to back up.
- On the Exclusions tab, you specify exclusions to the the content that you specified in the exceptions list.
Procedure
- From the navigation pane, go to Protect > File servers. The File servers page appears.
- In the Actions column for the server, click the action button, and then click Edit plan association. The Edit plan dialog box appears. The plan associated with the file server and the backup content defined in the plan are displayed.
- Move the Define your own backup content toggle key to the right.
- Complete the following steps to add customized content:
| Option | On tabs | Steps |
|---|---|---|
| Enter custom path | Content Exclusions Exceptions | Type a path, and then click the add button |
| Browse | Content Exclusions Exceptions | 1. Click Browse. The Select a path dialog box appears. 2. Select a file or folder. 3. Click Save. The path is added to the Files and folders table. |
| Content Library | Content Exclusions | Use the Content Library to select well known folders, such as Desktop, and file types. 1. Click Content Library. The Add content dialog box appears. 2. Select content. 3. Click Save. The path is added to the Files and folders table. |
| Impersonate user | Content | Use Impersonate user to use a saved user credential to access the file system. 1. Click Impersonate user. The Impersonate user dialog box appears. 2. From the Credential list, select the user credential. 3. Click OK. |
| Files and folders | Content Exclusions Exceptions | Select the check boxes. Important: If you do not select a check box, then that content is not included, excluded, or excepted from the exclusions. |
| Include global exclusion filters | Exclusions | From the list, select one of the following options: – Use cell level policy (default): Enables or disables the global exceptions for the default subclient depending on whether the Use global filters on all subclients option is enabled for the environment. – On: Enables the global exceptions for the default subclient. – Off: Disables the global exceptions for the default subclient. |
- Click Save.
Microsoft Azure
You can configure your Azure blobs and files to back up directly to Metallic Azure storage without installing additional hardware or software. You can also back up Azure blobs and files to your own Azure storage.
Avoid Egress Charges
To avoid paying Azure egress charges, the Azure region the storage is located in must be the same Azure region that you back up to. For example, if you are backing up a blob located in Central US, the backup storage must also be located in Central US.
Supported Azure Regions
- Central US
- East US
- East US 2
- North Central US
- South Central US
- West Central US
- West US
- West US 2
- Canada Central
- Canada East
- Australia Central (Canberra)
- Australia Central 2 (Canberra)
- Australia East (New South Wales)
- Australia Southeast (Victoria)
- UK South
- UK West
- West Europe
- North Europe
- Norway East
Accessing the object storage overview
To perform operations on your Azure blob, open the object storage overview page.
Procedure
- Go to the Hub.
- On the Core tab, in the Protected Data Sources tile, above Object Storage, click the number.
The Object storage page appears. - In the Name column, click the object storage that you want to open.
Azure Blob
You can configure your Azure blob to back up directly to Metallic Azure storage without installing additional hardware or software. You can also back up your Azure blob to your own Azure storage.
To back up multiple storage accounts, configure each storage account individually.
Data Flow
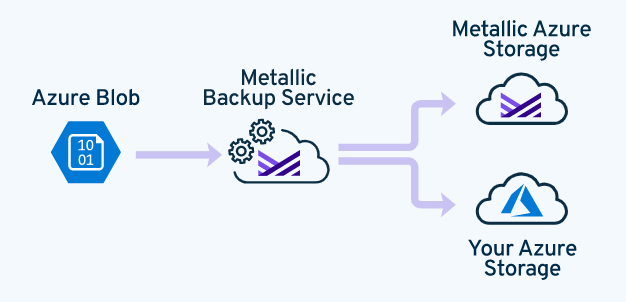
Restoring an Azure Blob in Place
To restore an Azure blob backup to its original location, use the in-place restore operation.
Procedure
- From the navigation pane, go to Protect > Object storage.The Object storage page appears.
- In the Object storage table, right-click the object storage repository that you want to restore, and then click Restore.
The Backup content page appears. - In the backup content list, select the backups to restore, and then click Restore.
The Restore options dialog box appears. - On the In place tab, specify the following information:
- No of streams: Enter the number of streams to use for the restore operation.
- Select one of the following:
- Overwrite files unconditionally
- Overwrite files only if the backed up file is newer
- Click Submit.
Restoring an Azure Blob Out of Place
To restore an Azure blob backup to a different blob (not the original blob), use the restore out-of-place operation.
Procedure
- From the navigation pane, go to Protect > Object storage.
The Object storage page appears. - In the Object storage table, right-click the object storage repository that you want to restore, and then click Restore.
The Backup content page appears. - In the backup content list, select the backups to restore, and then click Restore.
The Restore options dialog box appears. - On the Out of place tab, specify the following information:
- Destination target: Type the path to the target.
- No of streams: Type the number of streams to use for the restore operation.
- Destination path: Type the full restore location path.
- Select one of the following:
- Overwrite files unconditionally
- Overwrite files only if the backed up file is newer
- Click Submit.
Azure Files
You can configure your Azure files to back up directly to Metallic Azure storage without installing additional hardware or software. You can also back up your Azure files to your own Azure storage.
To back up multiple storage accounts, configure each storage account individually.
Data Flow
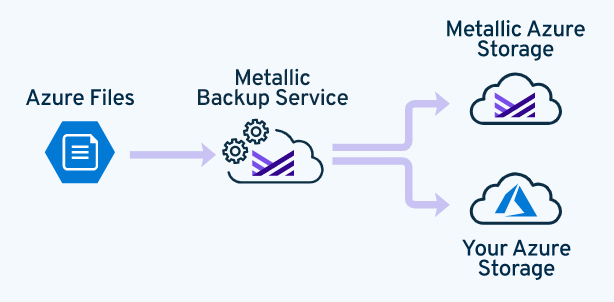
Restoring an Azure File in Place
To restore an Azure file backup to its original location, use the in-place restore operation.
Procedure
- From the navigation pane, go to Protect > Object storage.
The Object storage page appears. - In the Object storage table, right-click the object storage repository that you want to restore, and then click Restore.
The Backup content page appears. - In the backup content list, select the backups to restore, and then click Restore.
The Restore options dialog box appears. - On the In place tab, specify the following information:
- No of streams: Enter the number of streams to use for the restore operation.
- Select one of the following:
- Overwrite files unconditionally
- Overwrite files only if the backed up file is newer
- Click Submit.
Restoring an Azure File Out of Place
To restore an Azure file backup to a different location (not the original location), use the restore out-of-place operation.
Procedure
- From the navigation pane, go to Protect > Object storage.
The Object storage page appears. - In the Object storage table, right-click the object storage repository that you want to restore, and then click Restore.
The Backup content page appears. - In the backup content list, select the backups to restore, and then click Restore.
The Restore options dialog box appears. - On the Out of place tab, specify the following information:
- Destination target: Type the path to the target.
- No of streams: Type the number of streams to use for the restore operation.
- Destination path: Type the full restore location path.
- Select one of the following:
- Overwrite files unconditionally
- Overwrite files only if the backed up file is newer
- Click Submit.
Database
To store data in a cloud, use your own cloud or use the Metallic cloud. To store data on-premises, configure a backup gateway. Data can be stored directly on the backup gateway, or you can access other resources by using a UNC path.
Data flow

Subscription Usage for Databases
You can view usage and metering information in the Subscription Usage tile and the Subscription Usage report on the Hub.
Subscription Usage Tile
The Subscription Usage tile in the Hub displays the peak front-end size for database data protected from the start of the current month until today. The front-end size is the source data capacity before compression and deduplication.
If database data was protected for one or more days in the month, the data is counted as part of the peak front-end size for that month. The data is counted even if it is removed from a backup schedule or if backup data was deleted from the system. If the database data is not backed up in the following months, it is not counted as part of subscription usage for those months.
For example, if DB01 and DB02 (each with 1 GB capacity) are protected on the first day of the month, and DB01 is removed from the system later that month, the peak front-end size protected in the month is 2 GB. If DB01 is not backed up in the following month and DB02 is backed up, the peak front-end size protected in the month is 1 GB.
Subscription Usage Report
To access the Subscription Usage report, click the link in the Subscription Usage tile in the Hub. The Subscription Usage report lists the names of all the database servers or instances with front-end size protected from the start of the current month to today. Use this report to validate the subscription usage you are charged for.
User Account configuration for SQL Server
Windows Configuration
Users who perform backup operations must be local administrators so that they have full control over the registry folder and the installation folder.
User credentials are not set during the agent installation. By default, the local system account is used. To access the SQL Server databases to perform backup and restore operations, SQL sysadmin rights are required.
| SQL Server Is | User Account | Privileges |
|---|---|---|
| Member of a WorkGroup | Local administrator of the computer where the SQL Server resides, like computer_name\user1.Member of the SQL sysadmin fixed server role. | Able to back up any file and folder on the local computer to which the local group applies. |
| Member of a Domain | Member of the Local administrator group of the computer where the SQL Server resides, like domain\user1.Member of the SQL sysadmin fixed server role.The account must have interactive log on rights to the computer where the SQL Server resides or have Log on as Batch job rights in the Local security policy. | Able to back up any file and folder on the following entities: a computer in the domaina computer in a domain where a two-way trust relationship exist |
For more information about the SQL sysadmin privileges, go to the Microsoft Support website and search for Microsoft KB article 2926557, SQL Server VDI backup and restore operations require Sysadmin privileges.
Push installations
Applies to: Core installations for Windows, Linux, and Microsoft SQL Server
To install software on the server that you want to back up, you can push the software from the backup gateway to the server. To perform a push installation, you need the name of the server that you want to back up and the user credentials for the server.
To successfully perform a push installation, do the following:
- Verify that the backup gateway has network access to the server.
- Obtain system administrator (sysadmin) user credentials for the server.
- Windows computers: The Remote Registry service must be enabled and configured to automatically start during the computer startup.
Firewall and Network Port Requirements
Turn off the firewall services on the server, and temporarily open the following inbound network ports before performing the push installation:
- For UNIX, Linux, and Macintosh computers, enable SSH (Secure Shell), and then open port 22.
- For Windows computers, do the following:
- Open Port 135 for DCOM (Distributed Component Model).
- Open Port 139 for NetBIOS Session Service (if you are using legacy Windows computers, such as Windows NT or earlier versions).
- Open Port 445 for SMB (Server Message Block) file sharing.
- Open the Windows Management Instrumentation (WMI) port. For instructions on setting up a fixed port for WMI, see Setting Up a Fixed Port for WMI on the Microsoft website.
- Important: If Windows Firewall is enabled on the computer, do one of the following:
- Temporarily open the following ports in Windows Firewall:- Port 135 for DCOM-In (COM + Network Access) – Port 445 for SMB – WMI port
- Set up a remote cache in the network where the computer resides.
SAP HANA
You can use the Metallic software to back up and restore SAP HANA. SAP HANA is also supported in a multi-tenant environment.
Backups
Data You Can Back Up
- All of the database files on each of the nodes
- The log files on each of the nodes
- The catalog files
Data That Cannot Be Backed Up
- SAP HANA application profiles and binaries that are associated with the SAP HANA installation.
Backups You Can Perform
- Full backups
- Incremental backups
- Differential backups
When You Can Perform Backups
- On a schedule: The server plan that you assign manages scheduled backups
- On demand: You can perform on-demand backups at any time
Restores
Data You Can Restore
- Full Database: This restore operation includes the database and the log files
- Data Only
Backups You Can Use for Restores
- The most recent backup
- A backup from a specific date (point-in-time)
- A backup identified by a backup prefix or a internal backup job ID
Destinations You Can Restore To
- Destination server is where you performed the backup operation
- Destination server is different from where you performed the backup
SAP HANA Configuration
Configure SAP HANA.
Creating the SAP HANA HDBUSERSTORE KEY
To connect to the SAP HANA database by using the SAP HANA Secure User Store, create a SAP HANA HDBUSERSTORE key. Use a SAP HANA HDBUSERSTORE key instead of a user name and password so that users do not need to enter connection information.
Note: In a HANA replication setup, for example, if you have a replication system of HANA SID where the first two nodes (machine01 and machine 02) are master nodes, and the other two nodes (machine03 and machine04) are standby nodes, create the key on all nodes. When the master nodes are down and the standby nodes become the master nodes, the key will still remain valid and can connect to machine03 and machine04 when machine01 and machine02 are not available.
For information on the SAP Secure User Store, see hdbuserstore on the SAP website.
Before You Begin
Verify that the user associated with the HDBUSERSTORE key has the correct permissions:
- Backup operations: The DBA COCKPIT privilege is required. For more information, go to the SAP Documentation site, DBA Cockpit for SAP HANA: Authorizations. In the Database Users section, look at the Customer-specific user row.
To create a SAP HANA database user that has the required backup operation privileges, run the following SQL command:
CREATE USER MY_BACKUP_USER PASSWORD BackupOnly01 NO FORCE_FIRST_PASSWORD_CHANGE;
GRANT BACKUP ADMIN, DATABASE BACKUP ADMIN, CATALOG READ, INIFILE ADMIN TO MY_BACKUP_USER;
where MY_BACKUP_USER is the user name and BackupOnly1 is the password. The user must be created for the SYSTEMDB and all tenant databases, and the user must have the same password for each database. - Restore operations or clone operations: To run the CREATE or RENAME statements, the DATABASE_ADMIN privilege is required. For more information, see the SAP documentation site, System Privileges.
To create a SAP HANA database user that has the required restore operation privileges, run the following SQL command:
CREATE USER MY_RESTORE_USER PASSWORD RestoreOnly01 NO FORCE_FIRST_PASSWORD_CHANGE;
GRANT BACKUP ADMIN, DATABASE BACKUP ADMIN, DATABASE RECOVERY OPERATOR, CATALOG READ, INIFILE ADMIN, DATABASE START, DATABASE STOP, TRACE ADMIN, SERVICE ADMIN TO MY_RESTORE_USER;
Where MY_RESTORE_USER is the user name and RestoreOnly1 is the password. The user must be created for the SYSTEMDB and all tenant databases, and the user must have the same password for each database.
Note: The DATABASE BACKUP ADMIN and DATABASE RECOVERY OPERATOR privileges are supported on SAP HANA 2.0 SPS05 and later versions.
Procedure
- Log on as the <SID> admin in SAP HANA, on the command line, type the following command:su – <SID>adm
hdbuserstore -i set <key_name> <client_computer>:3NN13,<client_computer>:3NN15 <user_name> <password>
where NN is the HANA SID number starting from 00 to 99. Example:- If you have HANA SID with One Node (machine01 only) with the SID name X01 and instance number 10, use the following command:
su – x01adm
hdbuserstore -i set MYKEY machine01:31013,machine01:31015 SYSTEM Password@12 - If you have HANA SID with four nodes (machine01 to machine04) with SID name Y01 and instance number 99, then create the key only on the node that appears first in the SAP HANA database instance or on the node that the user has manually set to appear as the first node. You do not create the KEY on the other three nodes. To create the key, use the following command:
su – y01adm
hdbuserstore -i set MYKEY machine01:39913,machine01:39915,machine02:39913,machine02:39915,machine03:39913,machine03:39915,machine04:39913,machine04:39915
SYSTEM Password@12
- If you have HANA SID with One Node (machine01 only) with the SID name X01 and instance number 10, use the following command:
- On the command line, type the following command to verify the key information.
hdbuserstore LIST <KEY>
where, KEY is the SAP HANA HDBUSERSTORE key.
Example:- To verify one node HANA SID machine01:hdbuserstore list MYKEY
KEY MYKEY
ENV : machine01:31013,machine01:31015
USER: SYSTEM - To verify four node HANA SID machine01 to machine04:hdbuserstore list MYKEY
KEY MYKEY
ENV : machine01:39913,machine01:39915,machine02:39913,machine02:39915,machine03:39913,machine03:39915,machine04:39913,machine04:39915
USER: SYSTEM
- To verify one node HANA SID machine01:hdbuserstore list MYKEY
Creating the SAP HANA Parameter File
You must create a parameter file when you perform certain types of backups and restores.
A parameter file is required for the following use cases:
- Perform a cross-machine restore. This includes a restore for disaster recovery.
- Perform a backup or restore for a multi-instance configuration.
Procedure
- In the iDataAgent folder, on the host where you installed the SAP HANA agent, create the SAP HANA BACKINT parameter file.
For information about required and optional parameters, see SAP HANA BACKINT Configuration Parameters. - Create the /usr/sap/<SID>/SYS/global/hdb/opt/hdbconfig directory.
- To link the file to the specified location, on the command line, type the following command:
ln -s /opt/commvault/iDataAgent/param /usr/sap/<SID>/SYS/global/hdb/opt/hdbconfig/param
where param is the name of the parameter file. - In the SAP HANA Studio, set the Backint data and log parameter files to the new parameter file.
For information about configuring the files, see Configure a Third-Party Backup Tool on the SAP website.
Note: Enable the third-party log backup option. Set the option to true.
SAP HANA BACKINT Configuration Parameters
The following table defines the SAP HANA BACKINT configuration file parameters.
| Parameter | Example | Definition |
|---|---|---|
| CvInstanceName | CvInstanceName instance_name Example: CvInstanceName Instance001 | The name of the configured instance. This parameter is optional. |
| CV_restCopyPrec | CV_restCopyPrec copy_precedence Example: CV_restCopyPrec 2 | The copy precedence for the restore job. You must set this value to 0 if you restore from a selective copy. |
Enabling SSL Communication with the SAP HANA System
If the SAP HANA system is configured to use an SSL (Secure Sockets Layer) connection, you must enable the Metallic software to authenticate access to the SAP HANA system.
Before You Begin
If the SAP HANA environment uses a Secure Sockets Layer (SSL) connection, obtain the name of the SSL provider and the SSL trust store file that stores the CA-signed certificates.
Procedure
- From the navigation pane, go to Protect > Databases.
The Instances page appears. - Click the SAP HANA instance.The instance page appears.
- In the General section, click Edit.
The Edit SAP HANA instance dialog box appears. - Move the Enable SSL toggle key to the right, and then provide the following details:
- In the Service Provider box, type the service provider that is used for the SSL connection. For example, type commoncrpto.
- In the SSL Trust store box, type the trust store name for the SSL connection. For example, type sapcli.pse.
- Click Save.
SAP HANA Restores
You can restore a SAP HANA database to its current location (in place) or to a different location (out of place).
Restoring to the Current Location (In Place)
You can restore a SAP HANA database to its current location (in place). The SAP HANA software brings the database down before the restore and brings it back up after the restore is complete.
To recover only the data, perform the restore by using a full backup.
Before You Begin
If you want to restore the most recent backup data and log files, stop the SAP HANA replication. If you do not stop the SAP HANA replication, only the latest data is restored and the latest log is not restored.
Procedure
- From the navigation pane, go to Protect > Databases > DB Instances > instance.
The instance properties page appears. - In the Recovery points section, click Restore.
The Restore Options page appears. - In the Destination Database, select the database where you want to restore.
- Choose the database recovery option:
- To recover the database to a point-in-time, click Up to, and then select the date and time.
- To restore by specifying the backup prefix, in the Backup prefix box, type the backup prefix for the backup.
Note: The Metallic software creates the backup prefix by pre-pending the job ID to the backup prefix. For example, 4815976_COMPLETE_DATA_BACKUP. You do not need the catalog backup available with backint. - To restore by specifying the internal backup job ID, in the Internal Backup ID box, type the internal backup job ID.
Note: If you restore by specifying the internal backup job ID, then you must have the catalog backup available with backint. SAP HANA creates the internal backup ID.
- To verify that all the backups required for the recovery operation are available, select the Check Access check box.
- To initialize the log area after the restore, select the Initialize log area check box.
- To recover using delta backups, select the Use delta backups check box.
If you do not use a delta backup for the recovery option, the software only uses the log backups for recovery. - To send a notification email when the restore job completes, select the When the job completes, notify me via email.
- Click Submit.
Restoring to a Different Location (Out of Place)
You can restore a SAP HANA database to a different location (out of place). The SAP HANA software brings the database down before the restore and brings it back up after the restore is complete.
To recover only the data, perform the restore by using a full backup.
Before You Begin
- Verify that the restore environment has the same set of nodes and the instance SID name as the backup environment. If you modified the backup environment, then you must make the same modifications on the restore environment.
- Verify that the SAP HANA software version on the destination is the same version or higher than the software version.
- If you want to restore the most recent backup data and log files, stop the SAP HANA replication. If you do not stop the SAP HANA replication, only the latest data is restored and the latest log is not restored.
Procedure
- From the navigation pane, go to Protect > Databases > DB Instances > instance.
The instance properties page appears. - In the Recovery points section, click Restore.
The Restore Options page appears. - On the Out of place tab, in the Source database, select the source database from where you to restore.
- From the Destination Server list, select the destination host to use for the restore.
- From the Destination instance list, select the destination instance to use for the restore.
- To restore from a snapshot backup, in the HANA data directory box, click Browse and select the HANA directory.
The full path where the destination instance resides. For example, if the SAP HANA SID path is hana/data/SID, then set the Destination Instance SAP HANA directory to: /hana/data.
Note: This is required for IntelliSnap cross instance and cross machine restores. - Choose the database recovery option:
- To recover the database to a point-in-time, click Up to, and then select the date and time.
- To restore by specifying the backup prefix, in the Backup prefix box, type the backup prefix for the backup.
Note: The Metallic software creates the backup prefix by pre-pending the job ID to the backup prefix. For example, 4815976_COMPLETE_DATA_BACKUP. You do not need the catalog backup available with backint. - To restore by specifying the internal backup job ID, in the Internal Backup ID box, type the internal backup job ID.
Note: If you restore by specifying the internal backup job ID, then you must have the catalog backup available with backint. SAP HANA creates the internal backup ID.
- To verify that all the backups required for the recovery operation are available, select the Check Access check box.
- To initialize the log area after the restore, select the Initialize log area check box.
- To recover using delta backups, select the Use delta backups check box.
If you do not use a delta backup for the recovery option, the software only uses the log backups for recovery. - To send a notification email when the restore job completes, select the When the job completes, notify me via email.
- Click Submit.
Office 365
You can configure Office 365 applications to back up directly to the Metallic cloud without installing additional hardware or software. Protect data in the following Office 365 applications from accidental deletions, ransomware scenarios, and data corruption:
- Exchange Online
- SharePoint Online
- OneDrive for Business
- Teams
When it is time to recover data, you can find and recover as many files as you need, or you can restore an entire folder or mailbox to a point in time. Metallic eliminates “dumpster diving” or rummaging through the Office 365 recycle bin.
Data flow
Subscription Usage for Office 365
You can view usage and metering information in the Subscription Usage tile and the Subscription Usage report on the Hub.
Subscription Usage Tile
The Subscription Usage tile in the Hub displays the total number of unique users protected from the start of the current month until today. The way unique users are calculated differs for each Office 365 application:
- For Mailboxes, user mailboxes are counted as part of subscription usage. However, both user mailboxes and group mailboxes are protected.
- For SharePoint, when the tenant admin site URL is configured, all the users from the tenant subscription are counted as part of subscription usage.
- For OneDrive, if the OneDrive Quota feature is enabled for a user and the user logs on, the user is counted as part of subscription usage.
If a user was protected for one or more days in the month, the user is counted as part of the total user usage. The user is counted even if it is removed from a backup schedule or if backup data was deleted from the system within the same month. If the user is not backed up in the following months, it is not counted as part of subscription usage for those months.
For example, if User 1 and User 2 are protected on the first day of the month, and User 1 is removed from the system later that month, the total number of users protected in the month is two users. If User 1 is not backed up in the following month and User 2 is backed up, the total number of users protected in the month is one user.
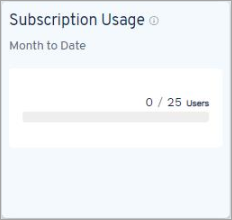
Subscription Usage Report
To access the Subscription Usage report, click the link in the Subscription Usage tile in the Hub. The Subscription Usage report lists the names of all the users protected from the start of the current month to today. Use this report to validate the subscription usage you are charged for.
Accessing Office 365 apps
To perform operations, such as restore operations, on an Office 365 application, you must open the application.
- Go to the Hub.
- On the Office 365 tab, in the Protected Data Sources tile, click the number of mailboxes, users, or sites that you are managing. The Office 365 apps page appears.
- In the App name column, click the app that you want to open. Tip: The Service type column displays the app type: Exchange Online, OneDrive for Business, or SharePoint.
Exchange Online
You can use Metallic to back up and to restore Exchange Online data.
To set up Exchange Online, you can use the express configuration option or the custom configuration option.
Retention
The index server is scanned every 24 hours. Messages that are eligible for data aging based on their received time and the rules defined in the plans are pruned.
Getting started with Exchange Online
To get started with backing up an Exchange Online mailbox, complete the following tasks:
- Review the considerations for express and custom configuration methods to determine the best choice for your organization.
- Add an app for Exchange Online using the express or custom configuration method:
- Add a mailbox.
- Perform a test backup and restore to confirm that the system is set up correctly.
- Enable automatic discovery of mailboxes so that users and groups are automatically included in future backup operations.
After you add a mailbox and enable automatic discovery of mailboxes, backup operations run according to the schedule and settings configured in the plan that you selected.
Backups automatically start at 8-hour intervals. By default, data retention is set to unlimited, but you can set it at the individual mailbox level. - Monitor backup activity to maintain a functional environment.
Configuration Methods for Exchange Online
There are two methods of configuration:
- Express: Use this method in environments where the same person performs the roles of a backup administrator, an Office 365 administrator, and an Azure administrator.
- Custom: Use the custom configuration method for any of the following reasons:
- You do not want to use the Office 365 global administrator account.
- You have MFA enabled for the global administrator account, which is not supported in the express configuration.
- In your organization, a different person performs the role of either a backup administrator, an Office 365 administrator, or an Azure administrator.
Express configuration for Exchange Online
Before you begin the automated setup and configuration of Office 365 with Metallic, check the following configurations in the Office 365 applications:
- You must have an Azure global administrator account. Using the global administrator account, Metallic automatically creates the Metallic backup app and registers with Azure AD.
- You must turn off Multi Factor Authentication (MFA) during the configuration process, and then turn on MFA again after the configuration process completes. For more information, in the Microsoft documentation, see Use Conditional Access Policies.
- Auto-generated service accounts must be excluded from any Modern Authentication policy and from any automatic password reset policy.
- The credentials from the global administrator account are used to create the service accounts that are required to discover user mailboxes and group mailboxes.
- After the Metallic app is configured, you can replace the global administrator role with the Exchange administrator role.
- Service accounts with the Exchange administrator role must be excluded from any automatic password reset policy.
Add an App for Exchange Online Using the Express Configuration Option
Use the express configuration option to create an Exchange Online app. After you create the Azure app that is needed for the Exchange Online app, the Metallic software automatically creates an Exchange Online service account for the Azure app, syncs the app with Azure, and authorizes the Azure app.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select Configure Exchange.
The Exchange Online page appears. - In the Name box, type a name for the app.
- From the Office 365 cloud region list, select the region that hosts Exchange Online:
- If Exchange Online is not hosted in a national cloud, select Default (Global Service).
- If Exchange Online is hosted in a national cloud, select the region.
- In the Connection settings section, enter the following information:
- Select Express configuration (Recommended).
- Enter the Office 365 global administrator account user name and password.
- Click Create Azure app.
A Microsoft window displays all the permissions that are required to access the Azure app. - Click Accept.
If the pop-up blocker appears in the browser, allow access to the Microsoft window so that you can accept the required permissions without interference.
- Click Save.
Custom configuration for Exchange Online
The custom configuration method is a manual process that requires the following actions and information:
- To set up modern authentication, complete these tasks:
- Register the Azure app with Azure.
- Provide service accounts access to Exchange Online shell.
- Obtain the Azure application ID, secret application key value, and Azure directory ID. For instructions about locating this information in the Azure Portal, in the Microsoft documentation, see Get tenant and app ID values for signing in.
- Obtain the Exchange Online service account log-on credentials.
Adding an App for Exchange Online Using the Custom Configuration Option
You can create the Exchange Online client manually by providing the Azure app details and Exchange Online service account login details.
Before You Begin
Complete the setup for Modern Authentication:
- Registering the application in the Azure portal to obtain the application ID, the Azure directory ID, and the application key value.
- Configuring the Exchange Online service account, and then using the Exchange Online service account login details to add the app.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select Configure Exchange.
The Exchange Online page appears. - In the Name box, type a name for the app.
- From the Office 365 cloud region list, select the region that hosts Exchange Online:
- If Exchange Online is not hosted in a national cloud, select Default (Global Service).
- If Exchange Online is hosted in a national cloud, select the region.
- In the Connection settings section, enter the following information:
- Select Custom configuration (Advanced).
- To enable modern authentication during a backup operation and a restore operation, move the Use modern authentication toggle key to the right.
- Click Add an Azure app.
The Azure application dialog box appears.- In the Application ID box, type the application ID.
- In the Application secret box, type the key value.
- In the Azure directory ID box, type the directory ID.
- Click Add.
- Click Add a service account.
The Exchange Online Service account dialog box appears.- In the Email address box, type the service account email ID.
- Type the associated password.
- Click Add.
- Click Save.
Basic Authentication
Basic authentication is also called legacy authentication.
Registering the Azure App for Exchange Online
Register the Exchange Online app with Microsoft Azure Active Directory (AD).
When you finish registering the app, record the Application ID and Directory ID. When you finish creating the client secret, record it. You will need to enter these values when you add an Exchange Online app.
To improve performance and to minimize throttling, you can register multiple apps. For example, for an Exchange Online app that has 2,500 mailboxes, register 5 apps. Every time an additional 1,000 mailboxes are added, register 1 additional app.
Disclaimer: You perform these steps in the Microsoft Azure Active Directory web application, which is subject to change without notice.
Log On to the Azure Portal as the Global Administrator
- Log on to the Azure portal (https://portal.azure.com/) using your global administrator account.
- Go to Azure Active Directory.
Register the Azure App
- In the navigation pane, click App registrations.
- Click New registration.
- In the Name box, enter a name for the app.
- Under Supported account types, select the accounts that you want to give access to the app.
- If you want to verify the status of the app and to authorize the app from the Command Center, under Redirect URI, enter the Command Center URL.
For example, enter https://Command_Center_name.domainname.com/adminconsole. - Click Register.
- Copy and paste the following values in a file or other document that you can access later:
- Application ID
- Directory ID
Request and Grant Permissions for Azure APIs
- In the navigation pane, click API permissions.
- Click Add a permission.
- Click Microsoft Graph.
- Click Application permissions.
- Select the following permissions:
- Directory: Directory.Read.All
- Group: Group.ReadWrite.All
- Click Add permissions.
- Click Add a permission.
- Click APIs my organization uses.
- On the search bar, type Office 365 Exchange Online.
- Select Office 365 Exchange Online, and then click Application permissions.
- Select full_access_as_app.
- Click Add permissions.
- Click Grant admin consent for tenant_name.
Create a Client Secret
- In the navigation pane, click Certificates & secrets.
- Click New client secret.
- Enter a description, and then select when you want the secret to expire.
- Click Add.
- Copy and paste the client secret value in a file or other document that you can access later.
You will enter this value in the Command Center when you create the Exchange Online app.
Providing Service Accounts Access to Mailboxes in Exchange Online (Through Azure Active Directory)
Applies to: Office 365 with Exchange, User Mailbox
In an Office 365 with Exchange environment, you must configure the Exchange Online service account to discover, archive, clean up, and restore data for user mailboxes, group mailboxes, and all public folders.
Before You Begin
The Office 365 with Exchange (Exchange Online) administrator account must have the following service accounts configured:
- Exchange Online service account, which must meet the following requirements:
- Must be an online mailbox or a shared mailbox.
- Must have multi-factor authentication enabled. You must provide the service account email address and the app password, which must be created so that the app can connect to Office 365. For more information, see Set up multi-factor authentication in the Office 365 admin center and Create an app password for Office 365 on the Microsoft documentation website. If MFA is enabled using the conditional access policy, then the app password cannot be configured.
- Must have either the Exchange administrator role or the global administrator role assigned so that the Exchange administrator or the global administrator can discover and back up Office365 group mailboxes. For more information, see Assign admin roles in Office 365 on the Microsoft documentation website.
- If you use more than one access node, the service account must have local logon rights.
- For public folders, you must have owner permissions at the root level and the sub-folder level. Convert the shared mailbox to a user mailbox, assign assign the owner permissions, and then convert the mailbox back to a shared mailbox.
- For the Exchange Online service account, a license is not required. Convert the user mailbox to a shared mailbox, and remove the Office 365 license for the Exchange Online service account.
- Local system account (Windows user), which must meet the following requirements:
- Must be a member of the local administrator group.
- Must be a domain user.
Procedure
- Open Windows PowerShell and create a remote PowerShell session to Office 365 with Exchange.
- To assign impersonation and view-only recipient permissions, type the following command:New-RoleGroup -Name “ExchangeOnlineBackupRoleGroup” -Roles “ApplicationImpersonation”, “View-Only Recipients” -Members serviceaccount1,serviceaccount2 where:
- ExchangeOnlineBackupRoleGroup is a unique name for the new role group.
- serviceaccount1 and serviceaccount2 are Exchange Online service accounts.
Modern Authentication
Modern authentication is a method of identity management that offers more secure user authentication and authorization.
Registering the Azure App for Exchange Online
Register the Exchange Online app with Microsoft Azure Active Directory (AD).
When you finish registering the app, record the Application ID and Directory ID. When you finish creating the client secret, record it. You will need to enter these values when you add an Exchange Online app.
To improve performance and to minimize throttling, you can register multiple apps. For example, for an Exchange Online app that has 2,500 mailboxes, register 5 apps. Every time an additional 1,000 mailboxes are added, register 1 additional app.
Disclaimer: You perform these steps in the Microsoft Azure Active Directory web application, which is subject to change without notice.
Log On to the Azure Portal as the Global Administrator
- Log on to the Azure portal (https://portal.azure.com) using your global administrator account.
- Go to Azure Active Directory.
Register the Azure App
- In the navigation pane, click App registrations.
- Click New registration.
- In the Name box, enter a name for the app.
- Under Supported account types, select the accounts that you want to give access to the app.
- If you want to verify the status of the app and to authorize the app from the Command Center, under Redirect URI, enter the Command Center URL.For example, enter https://Command_Center_name.domainname.com/adminconsole.
- Click Register.
- Copy and paste the following values in a file or other document that you can access later:
- Application ID
- Directory ID
Request and Grant Permissions for Azure APIs
- In the navigation pane, click API permissions.
- Click Add a permission.
- Click Microsoft Graph.
- Click Application permissions.
- Select the following permissions:
- Directory: Directory.Read.All
- Group: Group.ReadWrite.All
- Click Add permissions.
- Click Add a permission.
- At the bottom of the page, under Supported legacy APIs, click Exchange.
- Click Application permissions.
- Select full_access_as_app.
- Click Add permissions.
- Click Grant admin consent for tenant_name.
Create a Client Secret
- In the navigation pane, click Certificates & secrets.
- Click New client secret.
- Enter a description, and then select when you want the secret to expire.
- Click Add.
- Copy and paste the client secret value in a file or other document that you can access later.
You will enter this value in the Command Center when you create the Exchange Online app.
Providing Service Accounts Access to Mailboxes Exchange Online
You must configure the Exchange Online service account to discover, archive, clean up, and restore data for user mailboxes, group mailboxes, and all public folders.
Before You Begin
- Exchange Online service account, must meet the following requirements:
- Must be an online mailbox or a shared mailbox.
- Exchange administrator rights are required for running application check readiness.
- MFA must be disabled for the service account.
- Local system account (Windows user), which is required when more than one access node is used, must meet the following requirements:
- Must be a member of the local administrator group.
- Must be a domain user.
Procedure
- Open Windows PowerShell and create a remote PowerShell session to Office 365 with Exchange.
- To assign impersonation and view-only recipient permissions, type the following command:New-RoleGroup -Name “ExchangeOnlineBackupRoleGroup” -Roles “ApplicationImpersonation”, “View-Only Recipients” -Members serviceaccount1,serviceaccount2 where:
- ExchangeOnlineBackupRoleGroup is a unique name for the new role group.
- serviceaccount1 and serviceaccount2 are Exchange Online service accounts.
Add a Mailbox to the Exchange Online App
Add the mailboxes that you want the Exchange Online app to back up to the app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that you want to add the mailbox to.
The app page appears. - Click Add, and then click Add Mailbox.
The Add Mailbox dialog box appears. - From the Office 365 plan list, select the Exchange mailbox plan to use.
- From the Select mailboxes list, select the mailboxes to add to the Exchange Online app.
- Click Save.
Perform a Test Backup and Restore
To confirm that the Exchange Online app and mailboxes are set up correctly, perform a test backup and restore.
Back Up to Mailboxes
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the Exchange Online app.
The app page appears. - On the Mailboxes tab, select the mailboxes, and then click Back up.
A message prompts you to confirm submission of the backup job. - Click Yes.
Restore to Mailboxes
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the mailbox that you want to restore.
The app page appears. - On the Mailboxes tab, select the mailbox that you want to restore, click Restore, and then click Restore mailbox.
The Restore options dialog box appears, with options for restoring to the original location already selected. - For When message exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Click Submit.
Enabling Autodiscovery of Mailboxes
To discover mailboxes automatically, add the AD group to the Exchange Online app.
After you enable automatic discovery on the app, when a backup operation runs for one of the mailboxes, users groups are automatically discovered and included in the backup.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app to which you want to add the mailbox.
The app page appears. - On the Content tab, click Add, and then click Add AD group.
The Add AD group dialog box appears. - From the Exchange plan list, select a plan.
- From the Select AD groups list, select one or more mailboxes on which you want to enable autodiscovery.
- Click Save.
What to Do Next
To automatically discover new user accounts, run a backup operation on the autodiscovery-enabled mailboxes.
Restores
You can restore an individual mailbox item (such as folders, messages, and calendar appointments) or an entire mailbox.
Restoring an Individual Mailbox Item to Its Original Location
You can restore an individual Exchange Online mailbox item to the location that it was backed up from.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the item that you want to restore.
The app page appears. - On the Mailboxes tab, select the mailbox that contains the item that you want to restore, click Restore, and then click Restore messages.
The mailbox contents appear. - Select the item that you want to restore.
- Click Restore, and then click Selected items.
The Restore options dialog box appears, with options for restoring to the original location already selected. - For When message exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Click Submit.
Restoring a Mailbox to Its Original Location
You can restore an entire mailbox to the location that it was backed up from.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the mailbox that you want to restore.
The app page appears. - On the Mailboxes tab, select the mailbox that you want to restore, click Restore, and then click Restore mailbox.
The Restore options dialog box appears, with options for restoring to the original location already selected. - For When message exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Click Submit.
Downloading Exchange Online Folders or Messages
You can export folders or messages to an export set, change the format of the items to fit your needs, and download the exported PST or CAB file directly to your browser. When you export, an export set is automatically created.
The following file formats are supported when you export:
- PST (Portable Storage Table)
- CAB (cabinet file)
The default maximum size of export to PST or CAB is 25 GB. The size limitation applies to the total size of emails exported from the Office 365 client.
Note:
- When the export size exceeds 25GB, the export job does not start and an error message occurs. You can use the restore option or create multiple, smaller export sets.
- When multiple mailboxes are exported to a PST file, all the emails are exported from all the mailboxes into a single PST file.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Right-click the Office 365 app that contains what you want to export, and then click Restore.
The user mailbox appears in the folder view. - You can export a folder or messages:
Note: To include deleted items in the export file, click the action button , and then select Include deleted items.
, and then select Include deleted items.- To export a folder or a sub-folder, do the following:
- In the left pane, expand the mailbox, and then click the folder or the sub-folder.
- From the Export selected folder to list, select the file format.
- To export messages, do the following:
- Either expand folders to navigate to the messages, or in the Search box, enter search terms in the search filter list.
For example, enter inbox for the Folder filter. - Select the check boxes for the messages.
- From the Export selected items to list, select the file format.
The Export to dialog box appears.
- Either expand folders to navigate to the messages, or in the Search box, enter search terms in the search filter list.
- To export a folder or a sub-folder, do the following:
- In the Name box, type a name for the export set.
- If messages are selected, next to Selection Range, select the email messages to include in the export set:
- To select the selected email messages, click Selected.
- To select all the emails in the search results, select All.
- Click Submit.
A job runs to create the export set. - In the upper-right corner of the page, click View exports.
The View exports dialog box appears. The export sets that are ready to be downloaded and the export sets that are being created are listed. - To download the export set, click the download button
 .
.
Note: When mailboxes are exported, the folder hierarchy is maintained in the export set. - To delete an export set, select the check box for the export set, and then click Delete.
The message Selected exports deleted successfully confirms the deletion.
OneDrive for Business
You can use Metallic to back up and to restore Microsoft OneDrive for Business data.
Due to a known issue with Microsoft, the following items cannot be backed up or restored:
- Locally created OneNote files that were manually copied to OneDrive. This is due to an API limitation.
- OneNote files.
- OneNote notebooks stored in the Notebooks folder of the OneDrive account.
Getting Started with OneDrive for Business
To get started with backing up a OneDrive for Business user, complete the following tasks:
- Review the considerations for express and custom configuration methods to determine the best choice for your organization.
- Add an app for OneDrive for Business using the express or custom configuration method:
- Add a user.
- Perform a test backup and restore to confirm that the system is set up correctly.
- Enable automatic discovery of users so that they are automatically included in the future backup operations.
- Monitor backup activity to maintain a functional environment.
Configuration Methods for OneDrive for Business
There are two methods of configuration:
- Express: Use this method in environments where the same person performs the roles of a backup administrator, an Office 365 administrator, and an Azure administrator.
- Custom: Use the custom configuration method for any of the following reasons:
- You do not want to use the Office 365 global administrator account.
- You have MFA enabled for the global administrator account, which is not supported in the express configuration.
- In your organization, a different person performs the role of either a backup administrator, an Office 365 administrator, or an Azure administrator.
Express Configuration for OneDrive for Business
Before you begin the automated setup and configuration of Office 365 with Metallic, check the following configurations in the Office 365 applications:
- You must have an Azure global administrator account. Using the global administrator account, Metallic automatically creates the Metallic backup app and registers with Azure AD.
- You must turn off Multi Factor Authentication (MFA) during the configuration process, and then turn on MFA again after the configuration process completes. For more information, in the Microsoft documentation, see Use Conditional Access Policies.
- Auto-generated service accounts must be excluded from any Modern Authentication policy and from any automatic password reset policy.
- The credentials from the global administrator account are used to create the service accounts that are required to discover user accounts.
Add an App for OneDrive for Business Using the Express Configuration Option
Use the express configuration option to create an OneDrive for Business app. After you create the Azure app that is needed for the OneDrive for Business app, the Metallic software automatically creates an OneDrive for Business service account for the Azure app, syncs the app with Azure, and authorizes the Azure app.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select OneDrive.
The OneDrive for Business page appears. - In the Name box, type a name for the app.
- From the Office 365 cloud region list, select the region that hosts OneDrive for Business:
- If OneDrive for Business is not hosted in a national cloud, select Default (Global Service).
- If OneDrive for Business is hosted in a national cloud, select the region. Note: You cannot select China as the region.
Note: You cannot select China as the region.
- In the Connection settings section, enter the following information:
- Select Express configuration (Recommended).
- Enter the Office 365 global administrator account user name and password.
- Click Create Azure app.
A Microsoft window displays all the permissions that are required to access the Azure app.If the pop-up blocker blocks the Microsoft window, allow access to the Microsoft window. - At the bottom of the Microsoft window, click Accept.
- Click Save.
Custom configuration for OneDrive for Business
The custom configuration method is a manual process that requires the following actions and information:
- To set up modern authentication, register the Azure app with Azure.
- Obtain the Azure application ID, secret application key value, and Azure directory ID. For instructions about locating this information, in the Microsoft documentation, see Get tenant and app ID values for signing in.
- Obtain the OneDrive for Business service account log-on credentials.
Add an App Using Custom Configuration
You can create the OneDrive for Business app manually by providing the user details, Azure app details, and service account login details.
Before You Begin
- Obtain the application ID, the Azure directory ID, and the application key value by registering the application in the Azure portal. For information about registering the application, see Registering the Azure App for OneDrive for Business.
- Obtain the OneDrive for Business service account login details.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select OneDrive.
The OneDrive for Business page appears. - In the Name box, type a name for the app.
- From the Office 365 cloud region list, select the region that hosts OneDrive for Business:
- If OneDrive for Business is not hosted in a national cloud, select Default (Global Service).
- If OneDrive for Business is hosted in a national cloud, select the region.
Note: You cannot select China as the region.
- In the Connection settings section, enter the following information:
- Select Express configuration (Recommended).
- Enter the Office 365 global administrator account user name and password.
- Click Create Azure app.
A Microsoft window displays all the permissions that are required to access the Azure app.
If the pop-up blocker blocks the Microsoft window, allow access to the Microsoft window. - At the bottom of the Microsoft window, click Accept.
- Click Save.
Modern Authentication
Modern authentication is a method of identity management that offers more secure user authentication and authorization.
Tip: For modern authentication, create at least 3 apps.
Registering the Azure App
Register the Azure app with Microsoft Azure Active Directory (AD).
When you finish registering the app, record the Application ID and Directory ID. When you finish creating the client secret, record it. You will need to enter these values when you add an OneDrive for Business app.
Disclaimer: This procedure is performed using the Microsoft Azure Active Directory (Azure AD) Web application. The Azure AD application is subject to change without notice. Consult Microsoft documentation, for example “Azure Active Directory Documentation” (https://docs.microsoft.com/en-us/azure/active-directory/).
Log On to the Azure Portal as the Global Administrator
- Log on to the Azure portal (https://portal.azure.com/) using your global administrator account.
- Go to Azure Active Directory.
Register the Azure App
- In the navigation pane, click App registrations.
- Click New registration.
- In the Name box, enter a name for the app.
- Under Supported account types, select the accounts that you want to give access to the app.
- If you want to verify the status of the app and to authorize the app from the Metallic, under Redirect URI, enter the Metallic URL.
For example, enter https://Command_Center_name.domainname.com/adminconsole. - Click Register.
- Copy and paste the following values in a file or other document that you can access later:
- Application ID
- Directory ID
You will enter these values in the Metallic when you create the OneDrive for Business app.
Request and Grant Permissions for Azure APIs
- In the navigation pane, click API permissions.
- Click Add a permission.
The Request API permissions pane appears. - Click Microsoft Graph tile.
- Click Application permissions.
- Select the following permissions:
- Directory: Directory.Read.All
- Files: Files.ReadWrite.All
- User: User.Read.All
- Notes: Notes.ReadWrite.All
- Click Add permissions.
- Click Add a permission.
The Request API permissions pane appears. - Click SharePoint.
- Click Application permissions.
- Select the following permissions:
- Sites: Sites.FullControl.All
- User: User.Read.All
- Click Add permissions.
- Click Grant admin consent for tenant_name.
- Click Yes.
Create a Client Secret
- In the navigation pane, click Certificates & secrets.
- Click New client secret.
- Enter a description, and then select when you want the secret to expire.
- Click Add.
- Copy and paste the client secret value in a file or other document that you can access later.You will enter this value in the Metallic when you create the OneDrive for Business app.
Add a User to the OneDrive for Business App
Add the users that you want the OneDrive for Business app to back up to the app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the OneDrive for Business app.
The app page appears. - On the Users tab, click Add, and then click Add Users.
The Add user dialog box appears. - From the User group list, select a user group to add users to.
- From the Select users list, select the users to add.
- Click Add.
Perform a Test Backup and Restore of the OneDrive for Business Users
To confirm that the OneDrive for Business app and users are set up correctly, perform a test backup and restore.
Back Up the Users
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the row for the app, click the Action button, and then click Back up.
The Select backup level dialog box appears. - Click OK.
Restore the Users
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the row for the app, click the Action button, and then click Restore.
The Backup content page appears. - Select all the users, and then click Restore.
The Restore options dialog box appears, with options for restoring to the original location already selected. - Click Submit.
Enabling Autodiscovery of Users for OneDrive for Business
All users that belong to the user groups that you add (including users that are automatically added to the user groups) are included in backups of the app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the app to add the user group to.
The app page appears. - On the Content tab, click Add, and then click Add user group.
The Add user group dialog box appears. - In the User group name box, type a name for the user group.
- Complete one of the following steps to add users to the user group:
- On the Users tab, click Add user. Select the users you want to add, and then click Add.
- On the (.*) Regex patterns tab, click Add pattern. In the Regular expression box, type a regular expression or wildcard pattern, and then click Add.
You can enter multiple regular expressions or wildcard patterns.
- Click Save.
What to Do Next
To automatically discover new users, back up the OneDrive for Business app.
Automatic discovery options
To back up OneDrive user accounts, configure user groups to automatically discover user accounts. The user accounts that are discovered are added to user groups in the OneDrive app.
To perform a test backup operation, you can manually create a user group and then manually add a small number of user accounts to your user group.
Use either of the following options to automatically discover user accounts:
- Regular expressions or wildcards: If you use regular expressions, you can chose to automatically create user groups that alphabetically organize user accounts, or you can manually create user groups and then define your own regular expressions to discover user accounts
- Azure affinity groups
Autodiscovering user accounts using regular expressions or wildcards
You can use regular expressions or wildcards to autodiscover user accounts by UPN. For example, you can use regular expressions to discover all user accounts that contain “sales” in their UPN. The regular expressions that you use are case sensitive.
When you use regular expressions or wildcards to autodiscover user accounts, user accounts that match the regular expressions or the wildcard pattern are automatically assigned to the user-defined user group for which you enter the regular expressions or wildcards. If a user account does not match the expressions, then it is automatically assigned to the default user group.
| Regular expression | What the regular expression matches | Examples of UPN that match the regular expression |
|---|---|---|
| Sales* | UPN that begin with “sales” followed by any number of any characters | SalesA SalesOffice |
| [JT]im | UPN that begin with “J” or “T”, followed by “im”, and then followed by any number of any characters | Jim@xyz.abc Tim@xyz.abc |
| [a-k]Lee | UPN that begin with any character in the range of “a” through “k” inclusive, followed by “Lee”, and then followed by any number of any characters | aLee@xyz.abc bLee@xyz.abc |
| [A-Z]*[ ][A-E][A-Z]* | To skip the entire first name, find the first space and then discover users with last name beginning with the letters “A” through “E”. |
Before You Begin
Enable autodiscovery of user accounts, and then select Regex patterns. For more information, see Enabling Autodiscovery of User Accounts.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.The Office 365 apps page appears.
- Click the OneDrive for Business app.The app page appears.
- On the User groups tab, update an existing user group or create a user group:
- To add regular expressions to an existing user group, right-click the user group, and then select Manage.The user group page appears.
- To add regular expressions to a new user group, in the upper-right corner of the page, click Add user group.The Add user group page appears.
- On the Regex patterns tab, click Add pattern.The Add new content dialog box appears.
- In the Regular expression box, type a regular expression or wildcard pattern, and then click Add.You can enter multiple regular expressions or wildcard patterns.
- Click Save.
What to Do Next
Run a backup operation on this user-defined user group to back up all the user accounts that have UPN that match the regular expressions or the wildcard patterns that you entered.
Autodiscovering User Accounts for OneDrive for Business Using Azure Affinity Groups
You can use Azure affinity groups to autodiscover user accounts.
Before You Begin
Enable autodiscovery of user accounts, and then select Azure AD groups. For more information, see Enabling Autodiscovery of User Accounts.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the OneDrive for Business app.
The app page appears. - On the User groups tab, update an existing user group or create a user group:
- To add Azure AD groups to an existing user group, right-click the user group, and then select Manage.
The user group page appears. - To add Azure AD groups to a new user group, in the upper-right corner of the page, click Add user group.
The Add user group page appears.
- To add Azure AD groups to an existing user group, right-click the user group, and then select Manage.
- In the Content section, go to Add > Add group.
The Add new content dialog box appears. - Select the Azure affinity groups that you want to use to autodiscover user accounts, and then click Add.
- Click Save.
What to Do Next
Run a backup operation on this user-defined user group to back up all the user accounts that belong to the Azure affinity groups that you selected.
Creating a User Group for Testing
To perform a test backup operation, manually create a user group and then manually add a small number of user accounts to the user group.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the OneDrive for Business app.
The app page appears. - On the User groups tab, click Add user group.
The Add user group dialog box appears. - In the User group name box, type a name for the user group.
- From the Server plan list, select a plan.
- On the Users tab, click Add user.The Add new content dialog box appears.
- In the Name column, select the user accounts that you want to add.
- Click Add, and then click Save.
What to Do Next
After testing is complete, enable autodiscovery to automatically discover user accounts to back up.
Removing a User from an App
You can delete a user or a user group from a OneDrive for Business app. After you delete a user, you can still restore the user’s data.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the app that contains the user or the user group that you want to remove.
The app page appears. - On the Content tab, in the row for the user or the user group that you want to remove, click the action button
 , and then click Manage > Remove from content
, and then click Manage > Remove from content
.A confirmation dialog box appears. - Type DELETE, and then click Delete.
Excluding a User from Backups of a OneDrive for Business App
You can exclude a user or a user group from backups of a OneDrive for Business app. Excluding a user does not remove the user from the app, but the user’s data is not backed up.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the app that contains the user or the user group that you want to exclude.
The app page appears. - On the Content tab, in the row for the user or the user group that you want to exclude, click the action button
 , and then click Manage > Exclude from backup.
, and then click Manage > Exclude from backup.
A confirmation dialog box appears. - Type DELETE, and then click Delete.
OneDrive for Business Restore
You can restore OneDrive for Business users and files from backup operations.
Restoring a OneDrive for Business User
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
- The Office 365 apps page appears.
- On the Users tab, select the user group that you want to restore, and then click Restore > Restore user.
The Restore options page appears. - Select the users that you want to restore, and then click Restore.
The Restore options dialog box appears. - Under OneDrive account, select the restore destination:
- Restore the data to its original location
- Restore the data to another location
- To specify a different user, beside User, click Browse, and then select a user.
- To specify a different folder location, beside Folder, click Browse, and then select a folder or create a new folder.
- Under File options, for If the file exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Under Advanced Options, select an Office 365 client.
- Click Submit.
Restoring a OneDrive for Business User to Its Current Location
You can restore OneDrive for Business files.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
- The Office 365 apps page appears.
- On the Users tab, select the user group that you want to restore, and then click Restore > Restore files.
The Restore options page appears. - Select the users that you want to restore, and then click Restore.
The Restore options dialog box appears. - Under OneDrive account, select the restore destination:
- Restore the data to its original location
- Restore the data to another location
- Under File options, for If the file exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Under Advanced Options, select an Office 365 client.
- Click Submit.
You can use Metallic to back up and to restore SharePoint sites.
To get started with backing up a SharePoint Online site, complete the following tasks:
- Add an App Using Custom Configuration.
- Add a site.
- Perform a test backup and restore to confirm that the system is set up correctly.
- Monitor backup activity to maintain a functional environment.
The custom configuration method is a manual process that requires the following actions and information:
- To set up modern authentication, register the Azure app with Azure.
- Obtain the Azure application ID, secret application key value, and Azure directory ID. For instructions about locating this information, in the Microsoft documentation, see Get tenant and app ID values for signing in.
- Obtain the SharePoint Online service account log-on credentials.
Add an App using Custom Configuration
You can create the SharePoint Online app manually by providing the tenant details, Azure app details, and service account login details.
Before You Begin
- Obtain the application ID, the Azure directory ID, and the application key value by registering the application in the Azure portal. For information on registering the application, see Modern Authentication.
- Obtain the SharePoint Online service account login details.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select SharePoint.
The Region based storage for Office 365 data page appears. - From the Metallic storage by region list, select a region, and then click Next.
The SharePoint Online page appears. - In the Name box, type a name for the site.
- In the Tenant admin site URL box, type the URL for the tenant admin site.
For example, enter https://office_365_tenant_prefix-admin.sharepoint.com. - Type your login credentials for the SharePoint online administrator user account that can connect to the tenant, and that is also the site collection administrator.If you have two-factor authentication enabled, generate an app password and use the app password to connect to the tenant.
- Click Save.
The Office 365 apps page appears. - Click the SharePoint Online app.
The app page appears. - Click the Configuration tab, and complete the following steps:
a. To enable modern authentication during backups and restores, move the Use modern authentication toggle key to the right.
b. Click Add Azure app.
The Add Azure app dialog box appears.
c. In the Application ID box, type the application ID.
d. In the Application secret box, type the key value.
e. In the Azure directory ID box, type the directory ID.
f. Click Add.
g. Click Add a service account.
The SharePoint Online Service account dialog box appears.
h. In the Email address box, type the service account email ID.
i. Type the associated password.
j. Click Add. - Click Save.
Modern authentication is a method of identity management that offers more secure user authentication and authorization.
Registering the Azure App
For SharePoint Online backups to work in a modern authentication-enabled environment, you must create an Azure AD application and connect it to the tenant.
Disclaimer: This procedure is performed using the Microsoft Azure Active Directory (Azure AD) Web application. The Azure AD application is subject to change without notice. Consult Microsoft documentation, for example “Azure Active Directory Documentation” (https://docs.microsoft.com/en-us/azure/active-directory/).
Procedure
- Log on to the Azure portal (https://portal.azure.com/) using your global admin user account, and then go to Azure Active Directory.
- In the navigation pane, click App registrations.
The App registrations page appears. - To register the application, complete the following steps:
- Click New registration.
The Register an application screen appears.
a. In the Name box, type a name for the app.
b. Under Supported account types, select Accounts in this organizational directory only (<office_365_tenant_prefix> – Single tenant).
c. If you want to verify the status of the app and to authorize the app from the Metallic, under Redirect URI, enter the Metallic URL.
For example, enter https://Command_Center_name.domainname.com/adminconsole.
d. Click Register.
The app overview page appears.
e. Record the Application ID and the Directory ID.
You will enter these values later when you configure the Metallic environment. - In the navigation pane, click Certificates & secrets.
The Certificates & secrets page appears. - To create a client secret, complete the following steps:
- Click New client secret.
The Add a client secret dialog box appears. - Type a description, and then select when you want the secret to expire.
- Click Add.
- Use the Copy to clipboard button to copy the client secret value.
You will enter this value when later when you configure the Metallic environment.
- Click New client secret.
- To assign full permissions to the tenant to back up SharePoint sites, in your browser, go to the tenant URL.For example, go to https://<office_365_tenant_URL>/_layouts/15/appinv.aspx.
The Classic SharePoint admin center page appears. - In the App ID box, enter the application ID that you recorded earlier, and then click Lookup.
In the Title box, the name of the application appears. - In the App Domain box, type tenantname.onmicrosoft.com.
To get the correct domain name, go to the Microsoft Azure website, Custom domain names. - In the App’s Permission Request XML box, type the following XML string:
<AppPermissionRequests AllowAppOnlyPolicy="true">
<AppPermissionRequest Scope="http://sharepoint/content/tenant" Right="FullControl" />
<AppPermissionRequest Scope="http://sharepoint/social/tenant" Right="Read" />
</AppPermissionRequests> - Click Create.
- Click Trust It.
You must configure the SharePoint Online service account to discover, backup, and restore data for SharePoint sites.
- SharePoint Online service account, must meet the following requirements:
- SharePoint administrator or Office 365 user with PowerShell access rights are required for running licensing computation purposes.
- Security defaults is a tenant option that is not supported for licensing computation purposes.
- MFA must be disabled for the service account.
Add the sites that you want the SharePoint Online app to back up to the app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - Click the SharePoint Online app.
The app page appears. - In the Name box, type a name for the subclient.
- In the Max streams box, enter the number of streams to use for the backup operation.
- Click Add.
The Add content dialog box appears. - From the Office 365 plan list, select the plan to use for the sites.
- From the Sites list, select the sites to add.
- Click Add.
To confirm that the SharePoint Online app and sites are set up correctly, perform a test backup and restore.
Back Up the Sites
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the row for the app, click the Action button, and then click Back up.
The Select backup level dialog box appears. - Click OK.
Restore the Sites
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the row for the app, click the Action button, and then click Restore.
The Backup content page appears. - Select all the sites, and then click Restore.
The Restore options dialog box appears, with options for restoring to the original location already selected. - Click Restore.
You can restore SharePoint Online sites from backup operations.
You can restore a SharePoint Online site to its current location.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
- The Office 365 apps page appears.
- In the row for the app, click the Action button, and then click Restore.
The Backup content page appears. - Select the sites that you want to restore, and then click Restore.
The Restore options dialog box appears, with options for restoring to the original location already selected. - Under File options, for If the file exists, specify what to do with existing items:
- To overwrite existing items, select Overwrite unconditionally.
- To not overwrite existing items, select Skip.
- Under Advanced options, do the following:
- To restore the ACLs, select the Restore ACLs only check box.
- To restore the workflow definitions and alerts, select the Restore workflow definition and alerts only check box.
- Click Restore.
Teams
You can use the Metallic software to back up and restore Teams.
Backups
Data You Can Back Up
| Team item | Type of item | Backup | In-place restore |
|---|---|---|---|
| Teams | Private Teams Public Teams Org-wide Teams | Fully supported | Fully supported |
| Channels | Regular channel Private channel | Fully supported | Fully supported |
| Tabs | Posts Files Wikis Website Word, Excel, PowerPoint, and PDF document Libraries | Fully supported | Fully supported |
| Posts | Conversations Replies | Fully supported | Fully supported |
| Channel files | Files | Fully supported | Fully supported |
| Personal Chats | Chat Messages Files | With Exchange/OneDrive | Out-of-place only |
Backups You Can Perform
- Forever incremental
When You Can Perform Backups
- On a schedule: The server backup plan that you assign to the app manages scheduled backups
- On demand: You can perform on-demand backups at any time
Restores
Backups You Can Use for Restores
- Backups from any date/time, including the most recent backup
Destinations You Can Restore To
- The current location (in place)
- A different folder, a different team on a different channel (out of place)
- A different file location
Authentication
During backups and restores, the modern authentication is used to access user data.
Getting started with Teams
To get started with backing up Teams, complete the following tasks:
- Review the considerations for express and custom configuration methods to determine the best choice for your organization.
- Add an app for Teams using the express or custom configuration method:
- Add a Team.
- Perform a test backup and restore to confirm that the system is set up correctly.
- Enable automatic discovery of teams so that teams are automatically included in future backup operations.
After you add a team and enable automatic discovery of teams, backup operations run according to the schedule and settings configured in the plan that you selected. - Monitor backup activity to maintain a functional environment.
Configuration methods for Teams
There are two methods of configuration:
- Express: Use this method in environments where the same person performs the roles of a backup administrator, an Office 365 administrator, and an Azure administrator.
- Custom: Use the custom configuration method for any of the following reasons:
- You do not want to use the Office 365 global administrator account.
- You have MFA enabled for the global administrator account, which is not supported in the express configuration.
- In your organization, a different person performs the role of either a backup administrator, an Office 365 administrator, or an Azure administrator.
Express Configuration for Teams
Before you begin the automated setup and configuration of Office 365 with Metallic, check the following configurations in the Office 365 applications:
- You must have an Azure global administrator account.Using the global administrator account, Metallic automatically creates the Metallic backup app and registers with Azure AD.
- You must turn off Multi Factor Authentication (MFA) during the configuration process, and then turn on MFA again after the configuration process completes. For more information, in the Microsoft documentation, see Use Conditional Access Policies.
- Auto-generated service accounts must be excluded from any Modern Authentication policy and from any automatic password reset policy.
- When new channels are created, the global administrator credentials are used to assign service accounts to the group mailboxes that are created in the background.
- Teams group mailboxes will not be protected because only global administrator credentials can assign service accounts to group mailboxes.
Adding an App for Teams Using the Express Configuration Option
Use the express configuration option to create a Teams app. After you create the Azure app that is needed for the Teams app, the Metallic software automatically creates a Teams service account for the Azure app, syncs the app with Azure, and authorizes the Azure app.
Procedure
- Go to the Hub.
- On the Office 365 tab, from the New Configuration list, select Configure Teams.
The Teams page appears. - In the Name box, type a name for the app.
- In the Connection settings section, enter the following information:
- Select Express configuration (Recommended).
- Enter the Office 365 global administrator account user name and password.
- Click Create Azure app.
A Microsoft window displays all the permissions that are required to access the Azure app.
If the pop-up blocker blocks the Microsoft window, allow access to the Microsoft window. - At the bottom of the Microsoft window, click Accept.
- Click Save.
Custom Configuration for Teams
You can customize the configuration of the Teams app.
The custom configuration method is a manual process that requires the following actions:
- Register the Office 365 app with Azure.
- Request and grant permission for Azure APIs.
- Create a client secret for the Office 365 app.
- Obtain the Azure application ID, secret application key value, and Azure directory ID. For instructions about locating this information, in the Microsoft documentation, see Get tenant and app ID values for signing in.
Registering Teams with Azure
Register the Azure app with Microsoft Azure Active Directory (AD).
When you finish registering the app, record the Application ID and Directory ID. When you finish creating the client secret, record it. You need to enter these values when you add the app to the Metallic software.
To improve performance and to minimize throttling, you can register multiple apps.
For a Teams app that has 5,000 Teams items, register 5 apps. Every time an additional 1,000 Teams items are added, register 1 additional app.
Disclaimer: This procedure is performed using the Microsoft Azure Active Directory (Azure AD) Web application. The Azure AD application is subject to change without notice. Consult Microsoft documentation, for example “Azure Active Directory Documentation” (https://docs.microsoft.com/en-us/azure/active-directory/).
Log On to the Azure Portal as the Global Administrator
- Log on to the Azure portal (https://portal.azure.com/) using your global administrator account.
- Go to Azure Active Directory.
Register Teams in the Azure Portal
- In the navigation pane, click App registrations.
- Click New registration.
- In the Name box, enter a name for the app.
- Under Supported account types, select Accounts in this organizational directory only (<office_365_tenant_prefix> – Single tenant).
- To verify the status of the app and to authorize the app from the Metallic, under Redirect URI, enter the Metallic URL. For the Teams app, enter https://Command_Center_name.domainname.com/adminconsole/processAzureAuthToken.do
- Click Register.
- Copy and paste the following values in a file or other document that you can access later:
- Application ID
- Directory ID
You will enter these values in the Metallic software when you create the Office 365 app.
Request and Grant Permissions for Azure APIs for Azure Apps
- In the navigation pane, click API permissions.
- Click Add a permission.
- Click Microsoft Graph and complete the following steps:
a. Click Application Permissions.
b. Select the following permissions
Channel:Channel.Create
Channel:Channel.ReadBasic.All
ChannelSettings:Channel.Settings.ReadWrite.All
Files:Files.ReadWrite.All
Group:Group.ReadWrite.All
Sites:Sites.FullControl.All
Team:Team.ReadBasic.All
TeamMember:TeamMember.ReadWrite.All
User:User.Read.All
c. Click Delegated Permissions.
d. Select the following permissions:
ChannelMessage:ChannelMessage.Read.All
ChannelMessage:ChannelMessage.Send
Directory:Directory.AccessAsUser.All
Group:Group.ReadWrite.All
offline_access permission
openid permission
e. Click Add permissions. - On the app API permissions page, click Add a permission.
- Click APIs my organization uses and complete the following steps:
a. On the search bar, type Office 365 Exchange Online.
b. Select Office 365 Exchange Online, and then click Application permissions.
c. Select full_access_as_app.
d. Click Add permissions. - On the app API permissions page, click Grant admin consent for tenant_name.
Create a Client Secret
- In the navigation pane, click Certificates & secrets.
- Click New client secret.
- Enter a description, and then select Never expire.
- Click Add.
- Copy and paste the client secret value in a file or other document that you can access later.
You will enter this value in the Metallic software when you create the Office 365 app.
Adding an App for Teams Using Custom Configuration
You can create the Teams app manually by providing the Azure app details.
Before You Begin
You need an Office 365 licensed user account. The account will be added to the team that is being backed up.
Procedure
- Go to the Hub.
On the Office 365 tab, from the New Configuration list, select Configure Exchange.
The Exchange Online page appears. - In the Name box, type a name for the app.
- In the Connection settings section, enter the following information:
a. Select Custom configuration (Advanced).
b. Click Add an Azure app.
The Azure application dialog box appears.
i. In the Application ID box, type the application ID.
ii. In the Application secret box, type the key value.
iii. In the Azure directory ID box, type the directory ID.
iv. Click Add.
c. Click Acquire token.
The user that authorizes the app will be added as a member of all the teams that are going to be backed up.
i. Click Save.
Adding a Team to the Teams App
To back up a team, add the team to a Teams app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the Name column, click the app that you want to add a team to.
The app page appears. - Click Add, and then click Add team.
The Add team dialog box appears. - From the Office 365 plan list, select a plan.
- From the Teams list, select the items that you want to add to the app.
- Click Add.
Perform a Test Backup and Restore of a Team
To confirm that the Teams app and teams are set up correctly, run a backup operation followed by a restore operation.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click a Teams app.
The app page appears. - On the Teams tab, select the a team, click the action button, and then click Back up.
A message prompts you to confirm submission of the backup job. - Click Yes.
Restoring a Team
- From the navigation pane, go to Protect > Applications > Office 365.
- The Office 365 apps page appears.
- In the App name column, click the app that contains the team that you want to restore.
The app page appears. - On the Teams tab, select the team that you want to restore, click Restore, and then click Restore team.
The Restore options dialog box appears. - For File options, specify what to do with existing files:
- To not overwrite existing files, select Skip.
- To overwrite existing files, select Unconditionally overwrite.
- Click Submit.
Enabling Autodiscovery of Teams
Restoring a Team
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the team that you want to restore.
The app page appears. - On the Content tab, click Add, and then click All Teams.
The Add team dialog box appears. - From the Office 365 plan list, select a plan, and then click Add.
- Click Save.
What to Do Next
To automatically discover new user accounts, run a backup operation on the autodiscovery-enabled teams.
Configuration for Teams
You can configure the content that is included in Teams backup operations.
Removing an Item from a Teams App
You can remove an item from a team.
The next autodiscovery will discover the removed item, and the item will be added back to the app.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the Actions column of the Team that you want to remove the item from, click the Action button
 , and then click Manage > Remove from content.
, and then click Manage > Remove from content.
A confirmation dialog box appears. - Click Yes.
Tip: To see items that were removed, on the Content tab, click the gear icon ![]() , and then select Clear all filters. After you clear the filters, in the table column heading, click the Column Settings
, and then select Clear all filters. After you clear the filters, in the table column heading, click the Column Settings ![]() , and then click Column > Status. The status column is added to the table that displays Active, Deleted, Do not Backup and Unprotected status for the item.
, and then click Column > Status. The status column is added to the table that displays Active, Deleted, Do not Backup and Unprotected status for the item.
Excluding an Item from a Teams App
You can exclude an item from a Teams app.
Excluding an item does not remove the item from the app, but the item will not be backed up after the next autodiscovery runs.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the Actions column of the Team that you want to remove the item from, click the Action button
 , and then click Manage > Exclude from backup.
, and then click Manage > Exclude from backup.
A confirmation dialog box appears. - Click Yes.
Tip: To see items that were excluded, on the Content tab, click the gear icon ![]() , and then select Clear all filters. After you clear the filters, in the table column heading, click the Column Settings
, and then select Clear all filters. After you clear the filters, in the table column heading, click the Column Settings ![]() , and then click Column > Status. The status column is added to the table that displays Active, Deleted, Do not Backup and Unprotected status for the item.
, and then click Column > Status. The status column is added to the table that displays Active, Deleted, Do not Backup and Unprotected status for the item.
Restores
You can restore an entire team, a channel, or Teams items such as posts, files, and wikis to the same location or to a different location. For files, in addition to in-place restore operation and out-of-place restore operation, you can also choose to restore to a file location.
Comparing Restore Operations
Depending on the location for the restore operation, you will see the following results:
| Data type | In place | Out of place |
|---|---|---|
| Teams | The team is restored under the same team. | The team is restored to a different team, and the destination team is updated with the source channel name. |
| Channel | If the destination selected is also a channel, then if the overwrite option is selected, content and settings are restored on the source channel. | |
| Post | Posts are restored with details from when the post was sent. Reactions to posts are not restored. | |
| Wiki | The wiki page is restored to the same team. | The wiki page is created in a different team or channel. |
| File | A file can be restored to a different team and channel, or a different client location. |
File Options
For any restore operation of teams, channels, posts, wikis, or files, you can choose the following file options:
- Skip: If the file already exists on the location, then it will be skipped during restore.
- Overwrite: If the file exists on the location, then it will be overwritten.
Restores for a Team in Teams
You can restore a team to its original location or to a team in a different location.
Original Location
Restore a team to its original location.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the team that you want to restore.
The app page appears. - On the Teams tab, select the team that you want to restore, click Restore, and then click Restore team.
The Restore options dialog box appears. - For File options, specify what to do with existing files:
- To not overwrite existing files, select Skip.
- To overwrite existing files, select Unconditionally overwrite.
- Click Submit.
Different Location
You can restore a team to another team.
Procedure
- From the navigation pane, go to Protect > Applications > Office 365.
The Office 365 apps page appears. - In the App name column, click the app that contains the team that you want to restore.
The app page appears. - On the Teams tab, select the team that you want to restore, click Restore, and then click Restore team.
- The Restore options dialog box appears.
- Under Microsoft Teams, click Restore the data to another location, and then click the Browse button.
The Select a team dialog box appears. - Select a team, and then click Select.
- For File options, specify what to do with existing files:
- To not overwrite existing files, select Skip.
- To overwrite existing files, select Unconditionally overwrite.
- Click Submit.
Endpoint
If you are using the Endpoint solution to back up user laptops and desktops, you can manage your endpoints by using the Hub.
Key Features
- Fully customizable, plan-based automatic backups: Secure protection for business-critical data on laptops and desktops through source-side deduplication, scheduling, and intelligent bandwidth throttling.
- Data loss prevention and remote wipe: Prevent unauthorized access to data on laptops by using file-level security that includes securely erasing data and locking sensitive files.
- End user self-service: End users can access their backed up data from smart phones, tablets, laptops, and desktops using mobile apps, a web-based portal and integrated file system plug-ins. End users can retrieve, manage, and view all of their protected files and e-mails in a cloud-based storage repository, and securely share files for collaboration.
- Fully automated deployment: IT administrators can centrally manage and automate mass deployment using mobile device management (MDM) services.
- Explorer Plugin for Windows: End users can access their backed up data and shares on the laptop using Windows explorer.
- Migration Assistant: To easily set up a new laptop, end users can move backed up data and user settings (appearance and personalization settings, browser settings, network settings, and more) from their old laptop to their new laptop.
Setup considerations
Add an antivirus exclusion for the installation path: Metallic_installation_directory\Metallic\Contentstore. For example, add c:\Program Files\Metallic\ContentStore.
If outbound traffic to TCP 80/443 is restricted, do the following:
- Log onto the Metallic hub.
- In the URL, look for the environment number.
For example, if your URL is m3.metallic.io, 3 is your environment number. - From the hub, create a support case that includes the environment number and your region.
*Note: If you are in multiple regions, include all of the regions in the support case. - After your receive the IP addresses, add them to your whitelist.
Endpoint hub
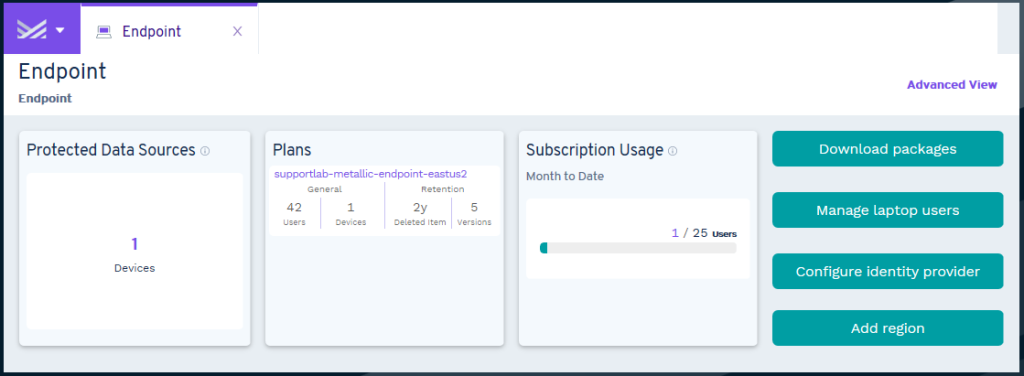
Subscription Usage for Endpoint
You can view usage and metering information in the Subscription Usage tile and the Subscription Usage report on the Hub.
Subscription Usage Tile
The Subscription Usage tile in the Hub displays the total number of unique users protected from the start of the current month until today.
If a user was protected for one or more days in the month, the user is counted as part of the total user usage. The user is counted even if it is removed from a backup schedule or if backup data was deleted from the system within the same month. If the user is not backed up in the following months, it is not counted as part of subscription usage for those months.
For example, if User 1 and User 2 are protected on the first day of the month, and User 1 is removed from the system later that month, the total number of users protected in the month is two users. If User 1 is not backed up in the following month and User 2 is backed up, the total number of users protected in the month is one user.
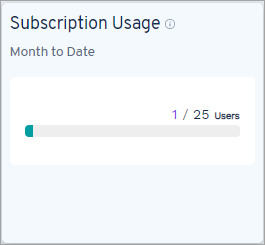
Subscription Usage Report
To access the Subscription Usage report, click the link in the Subscription Usage tile in the Hub. The Subscription Usage report lists the names of all the users protected from the start of the current month to today. Use this report to validate the subscription usage you are charged for.
Install software and authenticate users
To backup and monitor endpoint data, the Endpoint package must be installed on your users’ laptops and desktops. You can ask your users to download and to install the laptop package, or you can perform a silent installation of the laptop package. To decide which method to use in your environment, review the details of each method.
Interactive installations
| User authentication | Tenant administrator action | User action |
|---|---|---|
| Active Directory | Configure an Active Directory identity server. Distribute the link for the laptop package and the auth code to users. Users can also use their email addresses to register their laptops. | Download and install the laptop package, and then register the laptop or desktop with the auth code provided by the tenant administrator or your email address. |
| SAML | Configure an identity provider that supports SAML. Distribute the link for the laptop package and the auth code to users. | Download and install the laptop package, and then register the laptop or desktop with the auth code provided by the tenant administrator. |
| Local | Create users and automatically send the users email invitations. The email invitation contains a link for the laptop package and user credentials. | Download and install the laptop package, and then register the laptop or desktop with the credentials in the invitation email. |
Silent Installations
| User authentication | Tenant administrator action | User action |
|---|---|---|
| Active Directory | Configure an Active Directory identity server. Install the laptop package by using a third-party tool and the auth code. | None |
| SAML | Configure an identity provider that supports SAML. Install the laptop package by using a third-party tool and the auth code. | None |
Installing software by using a third-party tool
The Endpoint package can be pushed and installed using third-party software such as Microsoft System Center Configuration Manager (SCCM) or Jamf software.
Before you begin
Obtain the authorization code by going to the Hub, and then on the Endpoint tab, click Download Packages.
Procedure
Configure the third-party software to run the following command from the folder containing the laptop package contents.
- Windows Windows packages use a self-extracting executable that can be launched using a deployment tool with command line. The package must be pushed to the machine locally before running the command line. Running the package remotely over the network is not supported.
Win32_Client.exe /silent /install /silent /authcode authcodeWinX64_Client.exe /silent /install /silent /authcode authcode
Where authcode is the authorization code. The authorization code is required if the package does not contain user credentials for an installation user. - Macintosh Operating System (macOS) Silent macOS packages use the macOS pkg framework. These can be directly placed into the Jamf Casper software to run anytime. The package does not take arguments on command line, so you need to create a text file with the arguments, on the local macOS computer. On the local macOS computer, create an “install.ini” file in the global application support directory:
- Path to the ini file: /Library/Application Support/Commvault/install.ini
- Parameter inside the ini file: AUTH_CODE=”######” After creating the text file, you can push the macOS.pkg package to the client.
- UNIX Operating System For silent install on a UNIX machine, use the following:
./silent_install –authcode authcode
Where authcode is the authorization code. The authorization code is required if the package does not contain user credentials for an installation user. - For interactive or semi-silent install on a UNIX machine, use the following:
./cvpkgadd –authcode authcode
Where authcode is the authorization code. The authorization code is required if the package does not contain user credentials for an installation user.
Tasks
From the Endpoint Hub, you can perform the following tasks:
- Download packages for end-user laptops and desktops
- Manually add users if you do not use an identity provider
- Configure an identity provider
- Change what is backed up on user laptops and desktops
Download packages
To backup and monitor endpoint data, the Endpoint package must be installed on your users’ laptops and desktops. You can ask your users to download and to install the laptop package, or you can perform a silent installation of the laptop package. For more information about these methods, see Install software and authenticate users.
The Endpoint package is available for the following operating systems:
Linux
- Debian 9.x to Debian 10.x
- Fedora release 29 with glibc 2.28.x to Fedora release 30 with glibc 2.29.x
- Red Hat Enterprise Linux 7.x to Red Hat Enterprise Linux 8.x
- Ubuntu 8.04 to Ubuntu 18.10
Macintosh
- macOS Big Sur (v11.x)
- macOS Catalina (v10.15.x)
- macOS Mojave (v10.14.x)
- macOS High Sierra (v10.13.x)
- macOS Sierra (v10.12.x)
Windows
- Microsoft Windows 7 Editions to Microsoft Windows Client 10 Editions
Add users manually
To authenticate users with credentials stored in the Metallic backup service, manually add users. When you manually add users, you have the option to automatically send the users email invitations to download and install the Endpoint package on their laptops or desktops. The email invitation contains a link for to the Endpoint package and user credentials.
Note: If you configure an identity provider, you do not need to create users local to the Metallic backup service.
Configuring identity provider
To authenticate users with SAML, configure an identity provider. Common SAML identity providers include AD FS, Azure, and Okta.
Managing backup content
You can change what is backed up on user laptops and desktops.
By default, the following content is included or excluded when a laptop or desktop is backed up:
| Included | Excluded |
|---|---|
| Desktop folder Documents folder Office file extensions Pictures folder Image file extensions | Temporary Files (Windows, Mac, Linux) C:\Program Files C:\Program Files (x86) C:\Windows |
Procedure
- Go to the Hub.
- On the Endpoint tab, click Manage backup content.The Laptop plan page appears.
- On the General tab, in the Plan name box, type the name of the plan.
- Click Next.
- On the Backup content tab, click the Override base setting check box.
- Define the content to backup:
- On the Windows, Mac, or UNIX tab, beside Content to backup, click Add.
- In the Add content dialog box, browse for content to back up, or click Add custom content to type a path or pattern. For example, type *.docx to back up all files with the docx extension.
- To exclude some content from the content you are backing up, next to Exclude these files/folders/patterns, click Add.
- Click Save.
- Repeat these steps until content is added for each operating system that you want the plan to support.
- Click Next accepting all default values.
- Optional: On the Options tab, clear the check box for any alerts that you do not want to receive.
- Click Finish.
Restoring files and folders for a laptop or computer
You can restore backed-up data, including data that was previously deleted, to the same computer or laptop or a different computer or laptop.
Procedure
- Go to the Hub.
- On the Endpoint tab, in the Protected Data Sources tile, click the number of devices that you are managing. The Laptops page appears.
- In the Actions column for the laptop or computer that you want to restore, click the action button
 , and then click Restore. The Backup content page appears.
, and then click Restore. The Backup content page appears. - Browse for the files and folders that you want to restore. Tip: You can change the backup content you see by using the filter options in the upper-right corner of the page.
- To view data that was deleted from the previous backup operations, click the action button
 , and then click Show deleted items. Any previously deleted backed-up data appears.
, and then click Show deleted items. Any previously deleted backed-up data appears. - Select the check boxes for the files and folders that you want to restore.
- Click Restore. The Restore options dialog box appears.
- Choose how you want to restore the data:
- Destination client: Select the computer where you want to restore the data.
- Restore to original folder: (default) The option to restore data to the folder from where it was backed up. If you want to enter a new path in the Destination path box, clear this check box.
- Destination path: If you cleared the Restore to original folder check box, click Browse to choose a folder or to create a new folder. The data is restored to the folder that you choose or create.
- Unconditionally overwrite if it already exists: The option to overwrite files and folders on the destination laptop or computer with the files and folders you are restoring.
- Impersonate user: Select this option, and then, in the Username and Password boxes, enter the credentials for a user account that has permissions to execute the restore process on the destination computer.
- When the job completes, notify me via email: Select this option if you want to receive an email when the restore job completes.
- Click Submit.
Compliance Search
Use Compliance Search to search for information in structured or unstructured data within your organization. Compliance Search provides an intuitive interface for entering, categorizing and retrieving data securely, in compliance with security and data retention regulation.
Getting Started
After the Commvault team finishes setting up your Compliance Search environment, add compliance officers. Compliance officers perform searches to locate the information that is needed to satisfy regulatory compliance requirements.
Compliance Holds
To hold data for compliance purposes, you can set your user mailboxes to unlimited retention or to the retention term specified by your compliance mandate. Retention settings are on the plan that you associate with your mailboxes.
Creating compliance officers
To give users access to Compliance Search, create compliance officers.
Procedure
- Go to the Hub.
- In the User Management tile, click Manage > Compliance.
The eDiscovery user group properties page appears. - In the User section, click Add users.
The Add users dialog box appears. - You can add an existing user or a new user:
- To add an existing user, do the following:
- Next to the user, select the check box.
- Click Add.
- To add a new user, do the following:
- Click Add new user.
The Add user dialog box appears. - Enter the user information.
- Click Save.
The user properties page appears. - To return to the user group, click the name of the user group.
- Click Add new user.
- To add an existing user, do the following:
Accessing Compliance Search from the Hub
To search for email messages or files, you can open the Compliance Search search page from the Commvault Hub.
Note: If you are a Compliance Officer, access Compliance Search through the website address provided by your administrator.
Procedure
- Go to the Hub.
- On the Office 365 tab or the Endpoint tab, in the upper-right corner, click Compliance Search.
The Search page appears. - In the search box, type a keyword, and then click Search.
Search results appear in a tab. In the left pane, under Search Engine, the number of results for each search engine is displayed. Click a search engine to see the search results for that search engine. In the left pane, you can also click predefined filters to quickly filter the search results.
Basic Email Search Options for Compliance Search
Use these options to perform basic email searches from the Compliance Search search bar.
| Basic Search Options | Description |
|---|---|
| Search by Keyword | Type keywords into the search bar to search for messages that contain any of the entered keywords anywhere in the email message. Keyword searches are not case-sensitive. For example, searches that use the keywords monday or Monday will return the same results. |
| Search by Exact Phrase | To search using an exact phrase, place quotation marks before and after the phrase. For example, enter “today’s meeting notes” in the search bar to view results that contain this exact phrase. |
| Search by Sender | To search for emails from a particular sender, type from: in lower-case, followed by the sender’s name. For example, enter from: John Doe to search for emails sent from John Doe. You can also add quotation marks around the name to search by exact phrase. |
| Search by Recipient | To search for emails from a particular recipient, type to: in lower-case, followed by the recipient’s name. For example, enter to: John Doe to search for emails sent to John Doe. You can also add quotation marks around the name to search by exact phrase. Note: When you search for emails for a specific recipient, search results do not include messages sent to a distribution group the recipient belongs to unless you include the distribution group in your query. |
| Search by Subject | To search for emails with certain keywords in the subject line, type conv: in lower-case, followed by the keywords. For example, enter conv: monday’s meeting to search for emails that contain these words in the subject line. You can also add quotation marks around the keywords to search by exact phrase. |
Basic File Search Options for Compliance Search
Use these options to perform basic file searches from the Compliance Search search bar.
| Basic Search Options | Description |
|---|---|
| Search by Keyword | Type keywords into the search bar to search for files that contain any of the entered keywords anywhere in the text of the document. Keyword searches are not case-sensitive. For example, searches that use the keywords monday or Monday return the same results. |
| Search by Exact Phrase | To search using an exact phrase, place quotation marks before and after the phrase. For example, enter “today’s meeting notes” in the search bar to view results that contain this exact phrase. |
| Search by Location | To search for files within a particular location, type url: in lower-case, followed by the path of the directory. For example, enter url: C\:\\temp to search for files within the Temp folder on the C: drive. |
| Search by Title | To search for files within a specific title, type conv: in lower-case, followed by the path of the title. For example, enter conv: agenda to search for files with the title Agenda. You can also add quotation marks around the keywords to search by exact phrase. |
Wildcard Search
You can search for data using a wildcard character within a single keyword.
- To replace a single character with a wildcard, use the question mark ? symbol. For example, to search for best or test,you can search using the keyword ?est.
- To replace from zero to any number of characters with a wildcard, use the asterisk * symbol. For example, to search for bet, better, betting, you can search using the keyword bet*.
- You can use wildcard characters in the middle of a keyword. For example, to search for books, you can search using the keyword boo*s.
Considerations
- The wildcards are not supported within quotation marks ” “.
- Multiple wildcard characters cannot be included when searching for a phrase.
- Do not include a space before or after a wildcard character.
Creating Export Sets
You can create export sets in Compliance Search. Export sets are useful for preparing data or converting data to a uniform format such as CAB or PST.
Procedure
- In Compliance Search, perform a search.
- Click the check box next to the items that you want to add to the export set.
- Above the search bar, click Export To.
- Select the export format from the list.
- In the Export To dialog box, in the Export Set list, click Create New.
- Type the name of export set in the Export Set Name box.
Note: The following characters/ \ : * ? " < > | @ ; & ^ () % # +are not allowed in the name of an export set. - Optional: In the Description box, type the description.
- Click OK.
Downloading Search Results in Compliance Search
You can download your Compliance Search search results. If multiple files or emails are selected for download, the files or emails are downloaded as a zip file. If the file name contains Unicode characters, the file name changes after download.
Procedure
- From the search result window, select the files or emails to be downloaded.
- Above the search bar, click Download.
The files or emails are downloaded on your local disk at the destination folder specified by you.
The downloaded file name is converted to a hyperlink.
Monitoring the Backup Environment
You can monitor activity in your environment by creating alert definitions, viewing events, and viewing and controlling jobs.
Accessing reports
Use reports to view the most critical information gathered from your Metallic environment.
To get started with Metallic reports, run the following reports:
- SLA
- Audit Trail
- Backup Job Summary
- Restore Job Summary
Procedure
- Log on to the Command Center.
- From the navigation pane, click Reports.
The Reports page appears. - Click a report.
Viewing Triggered Alerts
An alert is triggered when conditions within the entity meet the criterion selected in the alert definition.
Procedure
- From the navigation pane, click Alerts. The Triggered alerts page appears.
- Review the alerts triggered from the alert definitions.
- To see the alert details, in the Alert info column, click the descriptive link.
Deleting Triggered Alerts
You can delete triggered alerts.
Procedure
- From the navigation pane, click Alerts. The Triggered alerts page appears.
- To delete alerts, do one of the following:
- To delete individual alerts, select the check box for the alert, and then click Delete.
- To delete all of the alerts, select the check box in the table header and click Delete.
Note: If there are pinned alerts in the list, they are deleted.
Creating an Alert
You can create alerts to provide automatic notification about operations, such as failed jobs.
Procedure
- From the navigation pane, click Alerts. The Triggered alerts page appears.
- In the upper-left area of the page, click Alerts definitions. The Alerts definition page appears.
- In the upper-right area of the page, click Add alert definition. The Add alerts definition dialog box appears.
- In the Alert name box, type a name for the alert.
- From the Alert type list, click the type of alert you want to create. For example, select Backup Job Failed.
- If the alert type has a variable in it, in the Value for X box, enter a value for the variable.For example, you must define the value for X for the Backup Delay by X Hrs alert type.
- Under Entities, select the entities to apply the alert to.
- Under Users, for each user to notify, do one of the following:
- Type the user email address.
- Type the user or user group name, and from the generated list, select the user or user group.
- Click Add.
- Click Save.
Viewing Events
The Events page provides information about jobs and other significant events. In some cases, events can trigger alerts to notify users of events (such as job failures).
Procedure
- From the navigation pane, click Events. The Events page appears.
- To view details for an event, in the Event ID column, click the event ID.
Viewing Jobs
You can view jobs for the entities in your application. For example, you can view jobs for servers or laptops.
All Jobs
Procedure
- From the navigation pane, go to Jobs. The Active jobs page appears.
Tip: You can change the jobs you see by using the filter options in the upper-right corner of the page.
- To view the job details, in the Job ID column, click the job ID.
For a Specific Entity
Procedure
- From the navigation pane, click the entity. For example, select Servers.
- In the table of available entities, in the Name column, click the entity. The entity properties page appears.
- In the upper right of the entity details page, click Jobs.
Note: Some entities have links to view specific types of jobs. For example, on the laptop details page, click Restore jobs to view the restore jobs for the laptop.
Controlling Jobs
You can control active jobs. For example, you can suspend a job.
Procedure
- From the navigation pane, go to Jobs. The Active jobs page appears.
Tip: You can change the jobs you see by using the filter options in the upper-right corner of the page.
- In the Actions column for the job, click the action button and choose your action:
- To kill the job, click Kill.
- To suspend the job, click Suspend.
- To resume a suspended job, click Resume.
Network connectivity
You must be able to connect to the proxies and domains associated with your Metallic environment. Outbound network connectivity is needed for data transfer, device registration, and portal access.
To allow outbound connectivity, obtain the region-specific proxy IP addresses and domains associated with your environment.
Procedure
- Log on to the Metallic hub.
- In the URL, look for the environment number.
For example, if your URL is m3.metallic.io, 3 is your environment number. - From the hub, create a support case that includes the environment number and your region.
*Note: If you are in multiple regions, include all of the regions in the support case. - After you receive the proxy IP addresses and domains, allow outbound connectivity.
Proxies and domains
Allow connectivity to the proxies and domains associated with your environment.
| Environment | Country | Address | Port |
|---|---|---|---|
| All | All | *.metallic.io | 80/443 |
| *.blob.core.windows.net | 443 | ||
| api.skyhookwireless.com | 443 | ||
| edc.commvault.com | 443 | ||
| 1 | Global/US | 40.123.45.235 40.79.32.105 |
443 |
| Australia | 20.193.2.126 40.82.219.107 |
443 | |
| France | 40.66.63.1 40.66.61.40 |
443 | |
| Japan | 40.81.189.67 40.81.187.89 |
443 | |
| UK | 51.11.28.66 40.81.158.7 |
443 | |
| 2 | Global/US | 52.252.15.17 52.177.30.214 |
443 |
| Canada | 52.228.123.134 52.228.124.35 |
443 | |
| 3 | Global/US | 40.70.227.193 40.70.227.196 |
443 |
| Canada | 52.228.121.30 52.228.121.96 |
443 | |
| France | 51.11.224.149 51.11.224.166 |
443 | |
| 4 | Global/US | 52.167.16.74 52.179.169.140 |
443 |
| India | 13.71.58.233 40.81.253.93 |
443 | |
| Australia | 20.193.31.161 20.53.69.143 |
443 |
Supported platforms and applications
You can back up data sources that meet the following requirements.
Applications
The following applications are supported.
Linux
- Microsoft SQL Server 2017 Editions up to the latest Service Pack
Windows
- Microsoft SQL Server 2019 Editions up to the latest Service Pack
- Microsoft SQL Server 2017 Editions up to the latest Service Pack
- Microsoft SQL Server 2016 Editions up to the latest Service Pack
- Microsoft SQL Server 2014 Editions up to the latest Service Pack
- Microsoft SQL Server 2012 Editions up to the latest Service Pack
- Microsoft SQL Server 2008 R2 Editions up to the latest Service Pack
- Microsoft SQL Server 2008 Editions up to the latest Service Pack
- Microsoft SQL Server 2005 Editions up to the latest Service Pack
Endpoints
The following operating systems are supported for laptops and desktops.
Linux
- Debian 9.x to Debian 10.x
- Fedora release 29 with glibc 2.28.x to Fedora release 30 with glibc 2.29.x
- Red Hat Enterprise Linux 7.x to Red Hat Enterprise Linux 8.x
- Ubuntu 8.04 to Ubuntu 18.10
Macintosh
- macOS Big Sur (v11.x)
- macOS Catalina (v10.15.x)
- macOS Mojave (v10.14.x)
- macOS High Sierra (v10.13.x)
- macOS Sierra (v10.12.x)
Windows
- Microsoft Windows 7 Editions to Microsoft Windows Client 10
File Servers
The following operating systems are supported.
Linux
- Debian 9.x
- Fedora release 29 with glibc 2.28.x
- Red Hat Enterprise Linux/CentOS 7.x with glibc 2.17.x and Red Hat Enterprise Linux/CentOS 8.x with glibc 2.28.x
- SuSE Linux (SLES) 11 to 15
- Ubuntu 8.04 to Ubuntu 18.10
Windows
- Microsoft Windows Server 2003 Editions to Microsoft Windows Server 2019 Editions: All editions except Nano Server
Hypervisors
The following hypervisors are supported.
VMware
- Streaming backups using vCenter Server versions 4.1 – 6.7 Update 2
Hyper-V
- Streaming backups using a Microsoft Windows Server or a Microsoft Hyper-V Server